 Your Instructor
Your Instructor  Exam Prep Tips
Exam Prep Tips

About CCNA Security Training
CCNA is course for networking this CISCO Router is the main component to build a computer network. This hands-on course is our recommended curriculum for those who want to upgrade, to building a network, maintain and troubleshoot networks. This course covers the range CISCO Routers . This is a preliminary course recommended for candidates wish to enter Network and System administration field
Cisco Certified Network Associate Security (CCNA Security) validates the knowledge and skills necessary to secure Cisco networks at the associated level. A network professional shows the skills needed to develop a security infrastructure with a CCNA Security certification, recognizes threats and vulnerabilities to networks, and mitigates security threats. The CCNA Security curriculum emphasizes core security technologies, installation, troubleshooting and monitoring of network devices to maintain data and devices integrity, confidentiality and availability, and competency in the technologies used by Cisco in its security structure.
A CCNA Security certification will enable you to develop a security infrastructure using Cisco network devices, acquire network device installation and monitoring skills, and recognize and control security structure threats. This latest version of CCNA Security course IINS v3 aims to deliver core security concepts, VPN encryption, secure access management, firewall, intrusion prevention, endpoint security along with email and web security.
Participants will learn how to install, troubleshoot, and monitor secure networks through this CCNA Security certification training to maintain confidentiality, device availability, and data and integrity.
After completing the CCNA Security training you will acquire skills to help you have a better understanding of the security threats and learn how to take preventive steps to stop such threats.
CCNA SECURITY TRAINING HIGHLIGHTS

Cisco CCNA Training Course Outline - CCENT
Video 1 - Introduction to CCENT
Video 2 - Introduction to Networking and the Networking Models
 What is A Network?
What is A Network?  The OSI Model
The OSI Model  The Data Transmission Process
The Data Transmission Process  The TCP/IP Model
The TCP/IP Model  Why Use Networking Models?
Why Use Networking Models?
 TCP And UDP - Part 1
TCP And UDP - Part 1  TCP And UDP - Part 2
TCP And UDP - Part 2  Ports
Ports  Sockets
Sockets  Port Numbers
Port Numbers
 The Need For And Operation of CSMA/CD
The Need For And Operation of CSMA/CD  Ethernet Types And Standards
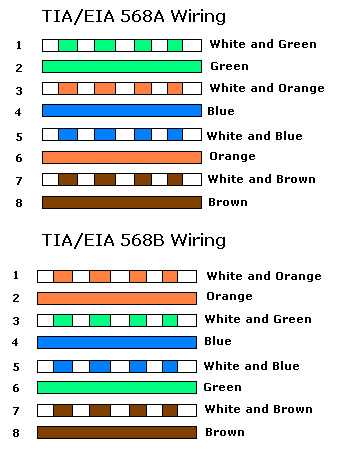
Ethernet Types And Standards  Pins And Transmissions
Pins And Transmissions  Crosstalk
Crosstalk
 Cable Types
Cable Types  Ethernet Addressing
Ethernet Addressing  Intro to WAN Cabling and a Cable Type Review
Intro to WAN Cabling and a Cable Type Review
Video 4 - Switching
 Repeaters, Hubs and Bridges
Repeaters, Hubs and Bridges  Building the MAC Table
Building the MAC Table  "Flood, Filter or Forward?"
"Flood, Filter or Forward?"  Frame Processing Methods
Frame Processing Methods  Virtual LANs
Virtual LANs  Cisco Three-Layer Switching Model
Cisco Three-Layer Switching Model  Introduction to STP
Introduction to STP  Basic Switch Security
Basic Switch Security  Port Security Defaults, Options and Configurations
Port Security Defaults, Options and Configurations
Video 5 - Common Router and Switch Commands
 Telnet and SSH
Telnet and SSH  User, Enable and Privilege Modes
User, Enable and Privilege Modes  Enable Password vs. Enable Secret
Enable Password vs. Enable Secret  "privilege level 15"
"privilege level 15"  Physical Side of Cisco Switches
Physical Side of Cisco Switches  Assigning an IP Address and Default Gateway To The Switch
Assigning an IP Address and Default Gateway To The Switch  Speed, Duplex, and "Interface Range"
Speed, Duplex, and "Interface Range"  Banners, "logging synch", and "exec-timeout"
Banners, "logging synch", and "exec-timeout"  Keystroke Shortcuts and Manipulating History
Keystroke Shortcuts and Manipulating History
 IP Addressing and Binary Conversions
IP Addressing and Binary Conversions  IP Address Classes
IP Address Classes  Private IP Address Ranges
Private IP Address Ranges  Intro to the Routing Process
Intro to the Routing Process  Keeping Subnets On One "Side" of the Router
Keeping Subnets On One "Side" of the Router
Video 7 - ARP, DNS and DHCP
 One Destination, Two Destination Addresses
One Destination, Two Destination Addresses  DNS and DHCP Process
DNS and DHCP Process  The ARP Process
The ARP Process  Routers, Broadcasts, and Proxy ARP
Routers, Broadcasts, and Proxy ARP  Configuring DHCP on a Cisco Router With SDM
Configuring DHCP on a Cisco Router With SDM
Video 8 - Memory Components and Config Files
 ROM, RAM, NVRAM, And Flash
ROM, RAM, NVRAM, And Flash  The Boot Process
The Boot Process  Setup Mode
Setup Mode  Startup And Running Configuration Files
Startup And Running Configuration Files  The COPY Command
The COPY Command  IOS Upgrading
IOS Upgrading  The Configuration Register
The Configuration Register
 Wireless Network Types
Wireless Network Types
 Standards and Ranges
Standards and Ranges
 Spread Spectrum
Spread Spectrum
 Antenna Types
Antenna Types
 CA vs. CD
CA vs. CD
 SSIDs and MAC Address Authentication
SSIDs and MAC Address Authentication
 WEP, WPA, and WPA2
WEP, WPA, and WPA2
Video 10 - Binary Math and Subnetting
 "The Secret" (Of Binary Success, That Is)
"The Secret" (Of Binary Success, That Is)  Decimal > Binary, Binary > Decimal
Decimal > Binary, Binary > Decimal  Subnetting Basics
Subnetting Basics  Calculating Number of Valid Subnets
Calculating Number of Valid Subnets  Prefix Notification
Prefix Notification
 Calculating Number of Valid Hosts
Calculating Number of Valid Hosts  Calculating Number of Valid IP Addresses in a Given Subnet
Calculating Number of Valid IP Addresses in a Given Subnet  Calculating the Subnet Number of a Given IP Address
Calculating the Subnet Number of a Given IP Address  Meeting Stated Design Requirements
Meeting Stated Design Requirements
Video 11 - Static Routing and RIP
 Static Routing Theory and Labs
Static Routing Theory and Labs  RIP Routing Theory and Labs
RIP Routing Theory and Labs  "show ip protocols", "show ip route rip", "debug ip rip", And More!
"show ip protocols", "show ip route rip", "debug ip rip", And More!

 Physical Side of WANs
Physical Side of WANs  Directly Connecting Cisco Routers Via Serial Interfaces
Directly Connecting Cisco Routers Via Serial Interfaces  HDLC and
HDLC and  Intro to Frame Relay
Intro to Frame Relay
 RFC 1918 Addresses, NAT and PAT
RFC 1918 Addresses, NAT and PAT
 Intro to ATM
Intro to ATM
 Modems and DSL Variations
Modems and DSL Variations
Video 13 - Troubleshooting
 Where to Begin
Where to Begin  Cisco Discovery Protocol (CDP)
Cisco Discovery Protocol (CDP)  L1 and L2 Troubleshooting
L1 and L2 Troubleshooting  LAN Troubleshooting
LAN Troubleshooting  WAN Troubleshooting
WAN Troubleshooting  Telnet and SSH Review and Maintenance Commands
Telnet and SSH Review and Maintenance Commands Administrative Distance
Administrative Distance  Extended Ping and Traceroute
Extended Ping and Traceroute  The Real Key to Troubleshooting
The Real Key to Troubleshooting
Video 14 - Introduction to Network Security
 Firewalls and Proxy Servers
Firewalls and Proxy Servers  The Attacker's Arsenal
The Attacker's Arsenal  Intro to PIX, ASA, IDS, and IPS
Intro to PIX, ASA, IDS, and IPS  Viruses, Worms, and Trojan Horses
Viruses, Worms, and Trojan Horses  Preventing Virus Attacks
Preventing Virus Attacks  One Final Cisco "Secret"
One Final Cisco "Secret"
Cisco CCNA Training Course Outline - ICND2
 Your Instructor
Your Instructor  CCNA Exam Paths
CCNA Exam Paths

Video 2 - Switching II
 STP
STP
 Root Bridges, Root Ports, and Designated Ports
Root Bridges, Root Ports, and Designated Ports
 STP Timers and Port States
STP Timers and Port States
 Portfast
Portfast
 VLANs and Trunking
VLANs and Trunking
 Access and Trunk Port Comparison
Access and Trunk Port Comparison
 VTP
VTP
 "Router on a Stick"
"Router on a Stick"
 RSTP and PVST
RSTP and PVST
 Etherchannels
Etherchannels
Video 3 - PTP WAN Links, HDLC, PPP, and Frame Relay
 HDLC vs. PPP
HDLC vs. PPP  PPP Features
PPP Features  PAP and CHAP
PAP and CHAP  Frame Relay Introduction
Frame Relay Introduction  Frame Relay LMI Theory
Frame Relay LMI Theory  Frame Relay Configs, DLCIs, Frame Maps, and Inverse ARP
Frame Relay Configs, DLCIs, Frame Maps, and Inverse ARP
 Frame Sub-Interfaces3
Frame Sub-Interfaces3  Split Horizon
Split Horizon  Frame Relay LMI Show, Debug, and Lab
Frame Relay LMI Show, Debug, and Lab  FECN, BECN, DE bits
FECN, BECN, DE bits  PVC Status Meanings
PVC Status Meanings
 Static Routing Theory and Configuration
Static Routing Theory and Configuration
 Distance Vector Protocol Behavior - Split Horizon and Route Poisoning
Distance Vector Protocol Behavior - Split Horizon and Route Poisoning
 RIP Theory and Version Differences
RIP Theory and Version Differences
 The Joy of "show ip protocols"
The Joy of "show ip protocols"
 RIP Limitations
RIP Limitations
 RIP Timers
RIP Timers
 Floating Static Routes
Floating Static Routes
Video 5 - OSPF
 IPv6 Theory and Introduction
IPv6 Theory and Introduction
 Zero Compression and Leading Zero Compression
Zero Compression and Leading Zero Compression
 IPv6 Reserved Addresses
IPv6 Reserved Addresses
 The Autoconfiguration Process
The Autoconfiguration Process
 OSPF v3 Basics
OSPF v3 Basics
 Transition Strategies
Transition Strategies
 NAT Theory and Introduction
NAT Theory and Introduction
 Static NAT Configuration
Static NAT Configuration
 Dynamic NAT Configuration
Dynamic NAT Configuration
 PAT Configuration
PAT Configuration
Video 6 - EIGRP
 Introduction to EIGRP
Introduction to EIGRP
 Successors and Feasible Successors
Successors and Feasible Successors
 EIGRP vs. RIPv2
EIGRP vs. RIPv2
 Basic Configuration
Basic Configuration
 Wildcard Masks
Wildcard Masks
 Load Sharing (Equal and Unequal-cost)
Load Sharing (Equal and Unequal-cost)
 EIGRP, RIPv2, and Autosummarization
EIGRP, RIPv2, and Autosummarization
 Passive vs. Active Routes
Passive vs. Active Routes
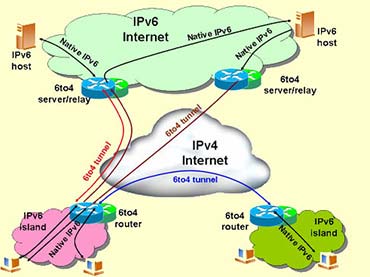
 IPv6 Theory and Introduction
IPv6 Theory and Introduction
 Zero Compression and Leading Zero Compression
Zero Compression and Leading Zero Compression
 IPv6 Reserved Addresses
IPv6 Reserved Addresses
 The Autoconfiguration Process
The Autoconfiguration Process
 OSPF v3 Basics
OSPF v3 Basics
 Transition Strategies
Transition Strategies
 NAT Theory and Introduction
NAT Theory and Introduction
 Static NAT Configuration
Static NAT Configuration
 Dynamic NAT Configuration
Dynamic NAT Configuration
 PAT Configuration
PAT Configuration
Video 8 - VPNs and IPSec
 Definitions and Tunneling Protocols
Definitions and Tunneling Protocols
 Data Encryption Technologies
Data Encryption Technologies
 Key Encryption Schemes
Key Encryption Schemes
 IPSec, AH and ESP
IPSec, AH and ESP
 A VPN in Your Web Browser
A VPN in Your Web Browser
Video 9 - ACLs and Route Summarization
 ACL Login and the Implicit Deny
ACL Login and the Implicit Deny
 Standard ACLs and Remarks
Standard ACLs and Remarks
 "Host" and "Any"
"Host" and "Any"
 The Order of the Lines
The Order of the Lines
 Extended ACLs
Extended ACLs
 Named ACLs
Named ACLs
 Telnet Access, Placing ACLs, and Blocking Pings
Telnet Access, Placing ACLs, and Blocking Pings
 Dynamic and Time-Based ACLs
Dynamic and Time-Based ACLs
 Port Number Review
Port Number Review
 Route Summarization with RIP and EIGRP
Route Summarization with RIP and EIGRP
