 Computer Fundamentals
Computer Fundamentals Generation of Computer
Generation of Computer

About Advanced Diploma in Hardware and Networking
Post Graduate Diploma in Computer hardware and Networking is Open to anyone with the Knowledge of English. This hands-on course is our recommended curriculum for those who want to upgrade, repair, maintain and troubleshoot computers. This course covers the full range of IBM and IBM-compatible systems. This is a preliminary course recommended for candidates wish to enter Network and System administration field.
Advanced Hardware and Networking Diploma is the course of Diploma Level Networking. The course provides a competitive edge for candidates in the IT world. Their technical skills include the ability to build a computer from scratch as well as computers and network configurations to optimize performance by implementing, managing and maintaining it. Course provides a cutting-edge domain for learners and allows them to build a machine from scratch.
After passing the course they can go for further Master’s Degree and then for research studies such as M.Phil. and Ph.D. They can have jobs mainly in professional, scientific and technical services, public administration and safety and financial and insurance services.
This skill-oriented course provides candidates with the necessary information to configure and manage OS Server, Networks, Router, L2/L3 Switch, Cloud Computing, Wireless & Security and equip them with the necessary skills to protect and recover computer systems & networks from various security threats.
Hardware and networking forms an integral part of IT sector. What is IT sector all about, you may ask. IT stands for Information Technology. This sector deals with storage, transmission, retrieval, processing and manipulation of data/information.
Highlights of Advanced Diploma in Hardware and Networking
Course Outcome-Post Graduate Advance Diploma in Hardware & Networking

[A]. DCA
 Computer Fundamentals, Computer Typing
Computer Fundamentals, Computer Typing
 Theory on Software, Hardware, Networking & Internetworking
Theory on Software, Hardware, Networking & Internetworking  Microsoft Windows Based Desktop Operating Systems
Microsoft Windows Based Desktop Operating Systems Microsoft Office Suit (Word, Excel, PowerPoint, Access)
Microsoft Office Suit (Word, Excel, PowerPoint, Access)
 Microsoft Office Suit (Outlook, Picture Manager, Project)
Microsoft Office Suit (Outlook, Picture Manager, Project) Productivity Product (Adobe Acrobat)
Productivity Product (Adobe Acrobat) Connectivity (LAN, Wireless, Remote Access)
Connectivity (LAN, Wireless, Remote Access)
 Internet (Browsing, E-Mail, Chat, Search Engines, download, Upload etc.)
Internet (Browsing, E-Mail, Chat, Search Engines, download, Upload etc.) Storage & Archive Services Scanning, Printing, Multimedia
Storage & Archive Services Scanning, Printing, Multimedia
[B]. HARDWARE COURSE CURRICULUM COMPTIA A+
Basics of Computer
Operating Systems
 MS-DOS Commands
MS-DOS Commands  Autoexec.bat & Config.sys
Autoexec.bat & Config.sys Working on Windows 98/XP
Working on Windows 98/XP
Memory Management
 Conventional & Extended Memory
Conventional & Extended Memory Types of Memory EDO, SDRAM, DDR, RAMBUS
Types of Memory EDO, SDRAM, DDR, RAMBUS
Assembling a PC
 Card and Connector Identification
Card and Connector Identification  Assembling a Latest PC
Assembling a Latest PC  Installation of Windows 98/XP
Installation of Windows 98/XP  Installation of Application Software
Installation of Application Software
Working on Windows 98/XP
 Start Menu
Start Menu  File Management
File Management  Configure using Control Panel
Configure using Control Panel  Adding and Removing the Drivers
Adding and Removing the Drivers  Intro of MS-Word, Excel & Powerpoint
Intro of MS-Word, Excel & Powerpoint
Digital Electronics
 Start Menu
Start Menu The Number System
The Number System Gates and Flip-Flop
Gates and Flip-Flop  Counter and Register
Counter and Register
Microprocessor and Support Chips
 Microprocessor Basics (8088)
Microprocessor Basics (8088) Microprocessor Internal Architecture
Microprocessor Internal Architecture  Bus Architecture (ISA, PCI, AGP etc.)
Bus Architecture (ISA, PCI, AGP etc.)  Support Chips (8284, 8288, 8237, 8259)
Support Chips (8284, 8288, 8237, 8259)
Advanced
Microprocessor
 Intel 80386, 80486, Celeron, P-II, P-III,PIV
Intel 80386, 80486, Celeron, P-II, P-III,PIV Non-Intel Processors (Cyrix, AMD)
Non-Intel Processors (Cyrix, AMD)  Math Co-Processors
Math Co-Processors  Advanced Motherboard Types
Advanced Motherboard Types
 Magnetic Memory
Magnetic Memory  Data Encoding Scheme
Data Encoding Scheme FDC and FDD
FDC and FDD HDD Interfaces
HDD Interfaces
 FDISK and FORMAT
FDISK and FORMAT HDD Organization
HDD Organization Optical Storage (CD, DVD)
Optical Storage (CD, DVD)
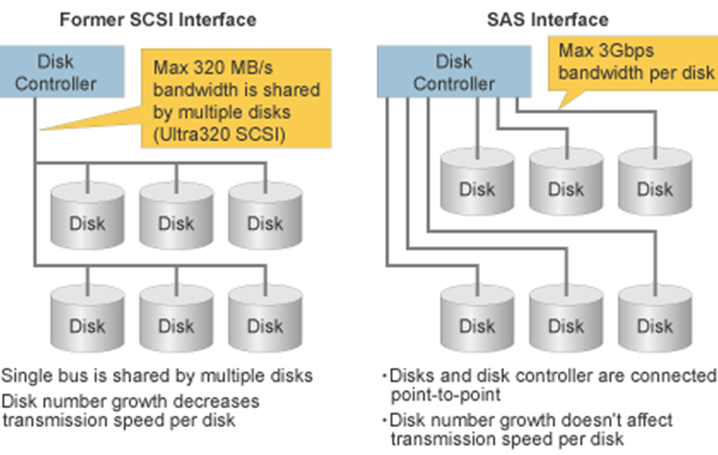
 HDD Interfaces
HDD Interfaces
Virus
 Types of Viruses
Types of Viruses  Virus Infection and Prevention
Virus Infection and Prevention Virus Scanning using Anti-Virus Software
Virus Scanning using Anti-Virus Software
Parallel and USB Port
 Parallel and USB Port Basics
Parallel and USB Port Basics  SPP/EPP/ECP
SPP/EPP/ECP Interfacing devices to USB and Parallel Port
Interfacing devices to USB and Parallel Port
Printers
 How Dot-Matrix, Inkjet & Laser Printer works
How Dot-Matrix, Inkjet & Laser Printer works  Loading the Drivers and enable print sharing
Loading the Drivers and enable print sharing
Serial Port and Modem
 Serial Port RS-232 Signals
Serial Port RS-232 Signals  Internal and External Modem
Internal and External Modem Configuring Modem for Internet connection
Configuring Modem for Internet connection
Laptop
 How Laptops are like Desktop
How Laptops are like Desktop  How Laptops are different from Desktop
How Laptops are different from Desktop Docking Connecto
Docking Connecto
Troubleshooting
 CMOS Setting
CMOS Setting Operating System Troubleshooting
Operating System Troubleshooting Hardware Troubleshooting
Hardware Troubleshooting
[C]. CompTIA Network+ Training Course Outline
What is a Network?
 Client/Server
Client/Server Peer-to-Peer
Peer-to-Peer LAN - Local Area Network
LAN - Local Area Network CAN - Campus Area Network
CAN - Campus Area Network MAN - Metropolitan Area Network
MAN - Metropolitan Area Network WAN - Wide Area Network
WAN - Wide Area Network How Do We Make Connections?
How Do We Make Connections? What is a Protocol?
What is a Protocol? Introduction to Addressing
Introduction to Addressing
Network Media
 Wired Media - Twisted Pair, Coaxial, and Fiber Optic
Wired Media - Twisted Pair, Coaxial, and Fiber Optic  What is the Plenum?
What is the Plenum? Common Connectors
Common Connectors Wiring Standards
Wiring Standards LAN Technology Types - Ethernet
LAN Technology Types - Ethernet Standard Ethernet
Standard Ethernet Fast Ethernet
Fast Ethernet Gigabit Ethernet
Gigabit Ethernet 10 Gigabit Ethernet
10 Gigabit Ethernet Wiring Distriburtion
Wiring Distriburtion
Network Topologies
 What Does Topology Mean?
What Does Topology Mean? Bus, Star, Ring, Mesh, Hybrid,
Bus, Star, Ring, Mesh, Hybrid,  WAN Technologies - Circuit and Pocket Switching
WAN Technologies - Circuit and Pocket Switching POTS, PSTN, T1/E1, and T3/E3
POTS, PSTN, T1/E1, and T3/E3 ISDN
ISDN SONET/OC-x
SONET/OC-x Frame Relay and ATM
Frame Relay and ATM MPLS - Multiprotocol Label Switching
MPLS - Multiprotocol Label Switching DSL
DSL Cable Modem, Satellite and Wireless
Cable Modem, Satellite and Wireless What is a VPN?
What is a VPN? What is a VLAN?
What is a VLAN?
 Definition of a Protocol
Definition of a Protocol
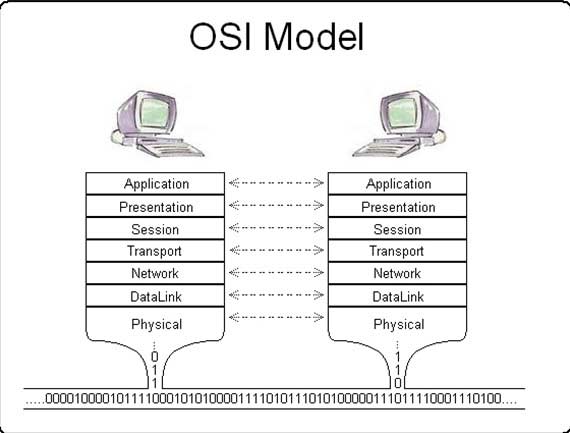
 Standards of Communication
Standards of Communication What is the OSI Model?
What is the OSI Model? Defining OSI Model Layers
Defining OSI Model Layers How Data Travels Through OSI Model
How Data Travels Through OSI Model Networking Hardware in OSI Model
Networking Hardware in OSI Model
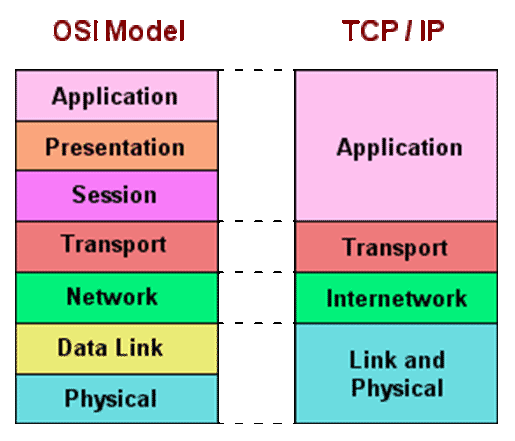
TCP/IP
 TCP/IP Protocol Suite
TCP/IP Protocol Suite
 What is TCP/IP (DARPA) Model?
What is TCP/IP (DARPA) Model?
 Transport Layer Protocols
Transport Layer Protocols
 Internet Layer Protocols
Internet Layer Protocols
 Types of TCP/IP Communication
Types of TCP/IP Communication
 Working with IP Addresses
Working with IP Addresses
 Planning an IP Addressing Scheme
Planning an IP Addressing Scheme
 Rules for IP Addressing
Rules for IP Addressing
 What is Classful IP Addressing?
What is Classful IP Addressing?
 Private vs. Public IP Addressing
Private vs. Public IP Addressing
 What is NAT?
What is NAT?
 How Computers Get IP Addresses
How Computers Get IP Addresses
 Working with Binary Numbers
Working with Binary Numbers
 Converting Binary to Decimal and Vice Versa
Converting Binary to Decimal and Vice Versa
 Binary IP Addresses
Binary IP Addresses
 Binary Subnet Masks
Binary Subnet Masks
 Internetworking - What is a Router?
Internetworking - What is a Router?
 What is a Default Gateway?
What is a Default Gateway?
 What is Subnetting?
What is Subnetting?
 Classful vs. Classless Interdomain Routing (CIDR)
Classful vs. Classless Interdomain Routing (CIDR)
 Subnetting with CIDR & VLSM
Subnetting with CIDR & VLSM
 CIDR Notation
CIDR Notation
 FTP - File Transfer Protocol
FTP - File Transfer Protocol
 TFTP - Trivial File Transfer Protocol
TFTP - Trivial File Transfer Protocol HTTP and HTTPS
HTTP and HTTPS NTP - Network Time Protocol
NTP - Network Time Protocol POP3 and IMAP4
POP3 and IMAP4 SMTP - Simple Mail Transfer Protocol
SMTP - Simple Mail Transfer Protocol
 DHCP - Dynamic Host Configuration Protocol
DHCP - Dynamic Host Configuration Protocol
 DNS - Domain Naming System
DNS - Domain Naming System Telnet and SSH
Telnet and SSH SNMP - Simple Network Management Protocol
SNMP - Simple Network Management Protocol SIP and RTP
SIP and RTP TLS - Transport Layer Security
TLS - Transport Layer Security
Network Devices
 Modem and NIC
Modem and NIC
 Repeater and Hub
Repeater and Hub
 Bridge and Switch
Bridge and Switch
 Router
Router
 Different Types of Switches
Different Types of Switches
 Advanced Switch Funcionality
Advanced Switch Funcionality
 Firewall and Proxy Server
Firewall and Proxy Server
 Wireless Access Point
Wireless Access Point
 Basic DHCP Server and DNS Server
Basic DHCP Server and DNS Server
 CSU/DSU
CSU/DSU
 Media Converters
Media Converters
 Load Balancer and Bandwidth Shaper
Load Balancer and Bandwidth Shaper
Routing
 Understanding Routing Tables
Understanding Routing Tables
 Adding and Deleting Routes
Adding and Deleting Routes
 Static vs. Dynamic Routing
Static vs. Dynamic Routing
 Routing Protocols
Routing Protocols
 Distance Vector Protocols: RIP, RIPv2, and BGP
Distance Vector Protocols: RIP, RIPv2, and BGP
 Link State Protocols: OSPF and IS-IS
Link State Protocols: OSPF and IS-IS
 Hybrid Routing Protocol: EIGRP
Hybrid Routing Protocol: EIGRP
 What is Convergence?
What is Convergence?
 IGP vs. EGP
IGP vs. EGP
Wireless Networking
 Benefits of Wireless Networking
Benefits of Wireless Networking
 Components of a Wireless Access Point
Components of a Wireless Access Point
 Where to Place a WAP
Where to Place a WAP
 Wireless Networking Standards
Wireless Networking Standards
 RF Channels
RF Channels
 How to Secure a Wireless Network
How to Secure a Wireless Network
 WEP - Wired Equivalency Privacy
WEP - Wired Equivalency Privacy
 WPA - Wi-Fi Protected Access
WPA - Wi-Fi Protected Access
 802.1x
802.1x
 Setting Up a Wireless Access Point
Setting Up a Wireless Access Point
 ipconfig/ifconfig/arp Utilities Overview
ipconfig/ifconfig/arp Utilities Overview
 ping/arp ping Utilities Overview
ping/arp ping Utilities Overview tracert/traceroute Utilities Overview
tracert/traceroute Utilities Overview mtr Utility Overview
mtr Utility Overview netstat/nbstat/route Utilities Overview
netstat/nbstat/route Utilities Overview nslookup/dig/host Utilities Overview
nslookup/dig/host Utilities Overview
 ipconfig Command
ipconfig Command
 arp Command
arp Command ping Command
ping Command
 tracert Command
tracert Command netstat Command
netstat Command
 nslookup Command
nslookup Command

Network Performance Optimization
 Reasons for Network Performance Optimization
Reasons for Network Performance Optimization
 Quality of Service (QoS)
Quality of Service (QoS) Traffic Shaping
Traffic Shaping Load Balancing
Load Balancing Fault Tolerance
Fault Tolerance RAID 0 - Disk Striping
RAID 0 - Disk Striping RAID 1 - Disk Mirroring and Duplexing
RAID 1 - Disk Mirroring and Duplexing RAID 5 - Disk Striping with Parity
RAID 5 - Disk Striping with Parity Other Popular Forms of RAID
Other Popular Forms of RAID Caching Engines
Caching Engines
Network Tools
 Cable Strippers
Cable Strippers
 Snips and Crimpers
Snips and Crimpers Punch Down Tool
Punch Down Tool Cable Testers and Certifiers
Cable Testers and Certifiers Time Domain Reflectometer (TDR) and Optical Time Domain Reflectometer (OTDR)
Time Domain Reflectometer (TDR) and Optical Time Domain Reflectometer (OTDR) Toner Probe
Toner Probe Voltage Event Recorder
Voltage Event Recorder Multimeter
Multimeter Protocol Analyzer, Temperature Monitor, and Butt Set
Protocol Analyzer, Temperature Monitor, and Butt Set

 Packet Sniffers
Packet Sniffers
 Port Scanners
Port Scanners Intrusion Detection Software (IDS) and Intrusion Prevention Software (IPS)
Intrusion Detection Software (IDS) and Intrusion Prevention Software (IPS) System, Event, and History Logs
System, Event, and History Logs
Documentation
 Why is Documentation so Important?
Why is Documentation so Important?
 What Should I Document?
What Should I Document? Wiring Schematics
Wiring Schematics Physical and Logical Network Diagrams
Physical and Logical Network Diagrams Baseline
Baseline Network Policies
Network Policies Network Procedures
Network Procedures Network Configuration
Network Configuration Regulations
Regulations
Troubleshooting
 The Process of Troubleshooting - Gather Information
The Process of Troubleshooting - Gather Information  Who is Affected?
Who is Affected? What's Changed?
What's Changed? Why is This Happening?
Why is This Happening? Can I Handle It?
Can I Handle It? Process of Finding a Solution
Process of Finding a Solution Physical Issues
Physical Issues Logical Issues
Logical Issues Issues to Escalate
Issues to Escalate Wireless Issues
Wireless Issues CMOS Setting
CMOS Setting Operating System Troubleshooting
Operating System Troubleshooting Hardware Troubleshooting
Hardware Troubleshooting
Network Security
 Firewalls
Firewalls  Other Security Devices
Other Security Devices Network Access Security
Network Access Security Filtering
Filtering Tunneling and Encryption
Tunneling and Encryption User Authentication
User Authentication Device Security
Device Security Common Security Threats
Common Security Threats
[D]. Cisco CCNA Training Course Outline - CCENT
Video 1 - Introduction to CCENT
 Your Instructor
Your Instructor  Exam Prep Tips
Exam Prep Tips
Video 2 - Introduction to Networking and the Networking Models
 What is A Network?
What is A Network?  The OSI Model
The OSI Model  The Data Transmission Process
The Data Transmission Process  The TCP/IP Model
The TCP/IP Model  Why Use Networking Models?
Why Use Networking Models?
 TCP And UDP - Part 1
TCP And UDP - Part 1  TCP And UDP - Part 2
TCP And UDP - Part 2  Ports
Ports  Sockets
Sockets  Port Numbers
Port Numbers
 The Need For And Operation of CSMA/CD
The Need For And Operation of CSMA/CD  Ethernet Types And Standards
Ethernet Types And Standards  Pins And Transmissions
Pins And Transmissions  Crosstalk
Crosstalk
 Cable Types
Cable Types  Ethernet Addressing
Ethernet Addressing  Intro to WAN Cabling and a Cable Type Review
Intro to WAN Cabling and a Cable Type Review

Video 4 - Switching
 Repeaters, Hubs and Bridges
Repeaters, Hubs and Bridges  Building the MAC Table
Building the MAC Table  "Flood, Filter or Forward?"
"Flood, Filter or Forward?"  Frame Processing Methods
Frame Processing Methods  Virtual LANs
Virtual LANs  Cisco Three-Layer Switching Model
Cisco Three-Layer Switching Model  Introduction to STP
Introduction to STP  Basic Switch Security
Basic Switch Security  Port Security Defaults, Options and Configurations
Port Security Defaults, Options and Configurations
Video 5 - Common Router and Switch Commands
 Telnet and SSH
Telnet and SSH  User, Enable and Privilege Modes
User, Enable and Privilege Modes  Enable Password vs. Enable Secret
Enable Password vs. Enable Secret  "privilege level 15"
"privilege level 15"  Physical Side of Cisco Switches
Physical Side of Cisco Switches  Assigning an IP Address and Default Gateway To The Switch
Assigning an IP Address and Default Gateway To The Switch  Speed, Duplex, and "Interface Range"
Speed, Duplex, and "Interface Range"  Banners, "logging synch", and "exec-timeout"
Banners, "logging synch", and "exec-timeout"  Keystroke Shortcuts and Manipulating History
Keystroke Shortcuts and Manipulating History

 IP Addressing and Binary Conversions
IP Addressing and Binary Conversions  IP Address Classes
IP Address Classes  Private IP Address Ranges
Private IP Address Ranges  Intro to the Routing Process
Intro to the Routing Process  Keeping Subnets On One "Side" of the Router
Keeping Subnets On One "Side" of the Router
Video 7 - ARP, DNS and DHCP
 One Destination, Two Destination Addresses
One Destination, Two Destination Addresses  DNS and DHCP Process
DNS and DHCP Process  The ARP Process
The ARP Process  Routers, Broadcasts, and Proxy ARP
Routers, Broadcasts, and Proxy ARP  Configuring DHCP on a Cisco Router With SDM
Configuring DHCP on a Cisco Router With SDM
Video 8 - Memory Components and Config Files
 ROM, RAM, NVRAM, And Flash
ROM, RAM, NVRAM, And Flash  The Boot Process
The Boot Process  Setup Mode
Setup Mode  Startup And Running Configuration Files
Startup And Running Configuration Files  The COPY Command
The COPY Command  IOS Upgrading
IOS Upgrading  The Configuration Register
The Configuration Register
 Wireless Network Types
Wireless Network Types
 Standards and Ranges
Standards and Ranges
 Spread Spectrum
Spread Spectrum
 Antenna Types
Antenna Types
 CA vs. CD
CA vs. CD
 SSIDs and MAC Address Authentication
SSIDs and MAC Address Authentication
 WEP, WPA, and WPA2
WEP, WPA, and WPA2

Video 10 - Binary Math and Subnetting
 "The Secret" (Of Binary Success, That Is)
"The Secret" (Of Binary Success, That Is)  Decimal > Binary, Binary > Decimal
Decimal > Binary, Binary > Decimal  Subnetting Basics
Subnetting Basics  Calculating Number of Valid Subnets
Calculating Number of Valid Subnets  Prefix Notification
Prefix Notification
 Calculating Number of Valid Hosts
Calculating Number of Valid Hosts  Calculating Number of Valid IP Addresses in a Given Subnet
Calculating Number of Valid IP Addresses in a Given Subnet  Calculating the Subnet Number of a Given IP Address
Calculating the Subnet Number of a Given IP Address  Meeting Stated Design Requirements
Meeting Stated Design Requirements
Video 11 - Static Routing and RIP
 Static Routing Theory and Labs
Static Routing Theory and Labs  RIP Routing Theory and Labs
RIP Routing Theory and Labs  "show ip protocols", "show ip route rip", "debug ip rip", And More!
"show ip protocols", "show ip route rip", "debug ip rip", And More!

 Physical Side of WANs
Physical Side of WANs  Directly Connecting Cisco Routers Via Serial Interfaces
Directly Connecting Cisco Routers Via Serial Interfaces  HDLC and
HDLC and  Intro to Frame Relay
Intro to Frame Relay
 RFC 1918 Addresses, NAT and PAT
RFC 1918 Addresses, NAT and PAT
 Intro to ATM
Intro to ATM
 Modems and DSL Variations
Modems and DSL Variations
Video 13 - Troubleshooting
 Where to Begin
Where to Begin  Cisco Discovery Protocol (CDP)
Cisco Discovery Protocol (CDP)  L1 and L2 Troubleshooting
L1 and L2 Troubleshooting  LAN Troubleshooting
LAN Troubleshooting  WAN Troubleshooting
WAN Troubleshooting  Telnet and SSH Review and Maintenance Commands
Telnet and SSH Review and Maintenance Commands Administrative Distance
Administrative Distance  Extended Ping and Traceroute
Extended Ping and Traceroute  The Real Key to Troubleshooting
The Real Key to Troubleshooting
Video 14 - Introduction to Network Security
 Firewalls and Proxy Servers
Firewalls and Proxy Servers  The Attacker's Arsenal
The Attacker's Arsenal  Intro to PIX, ASA, IDS, and IPS
Intro to PIX, ASA, IDS, and IPS  Viruses, Worms, and Trojan Horses
Viruses, Worms, and Trojan Horses  Preventing Virus Attacks
Preventing Virus Attacks  One Final Cisco "Secret"
One Final Cisco "Secret"
Cisco CCNA Training Course Outline - ICND2
 Your Instructor
Your Instructor  CCNA Exam Paths
CCNA Exam Paths

Video 2 - Switching II
 STP
STP
 Root Bridges, Root Ports, and Designated Ports
Root Bridges, Root Ports, and Designated Ports
 STP Timers and Port States
STP Timers and Port States
 Portfast
Portfast
 VLANs and Trunking
VLANs and Trunking
 Access and Trunk Port Comparison
Access and Trunk Port Comparison
 VTP
VTP
 "Router on a Stick"
"Router on a Stick"
 RSTP and PVST
RSTP and PVST
 Etherchannels
Etherchannels
Video 3 - PTP WAN Links, HDLC, PPP, and Frame Relay
 HDLC vs. PPP
HDLC vs. PPP  PPP Features
PPP Features  PAP and CHAP
PAP and CHAP  Frame Relay Introduction
Frame Relay Introduction  Frame Relay LMI Theory
Frame Relay LMI Theory  Frame Relay Configs, DLCIs, Frame Maps, and Inverse ARP
Frame Relay Configs, DLCIs, Frame Maps, and Inverse ARP
 Frame Sub-Interfaces3
Frame Sub-Interfaces3  Split Horizon
Split Horizon  Frame Relay LMI Show, Debug, and Lab
Frame Relay LMI Show, Debug, and Lab  FECN, BECN, DE bits
FECN, BECN, DE bits  PVC Status Meanings
PVC Status Meanings

 Static Routing Theory and Configuration
Static Routing Theory and Configuration
 Distance Vector Protocol Behavior - Split Horizon and Route Poisoning
Distance Vector Protocol Behavior - Split Horizon and Route Poisoning
 RIP Theory and Version Differences
RIP Theory and Version Differences
 The Joy of "show ip protocols"
The Joy of "show ip protocols"
 RIP Limitations
RIP Limitations
 RIP Timers
RIP Timers
 Floating Static Routes
Floating Static Routes
Video 5 - OSPF
 IPv6 Theory and Introduction
IPv6 Theory and Introduction
 Zero Compression and Leading Zero Compression
Zero Compression and Leading Zero Compression
 IPv6 Reserved Addresses
IPv6 Reserved Addresses
 The Autoconfiguration Process
The Autoconfiguration Process
 OSPF v3 Basics
OSPF v3 Basics
 Transition Strategies
Transition Strategies
 NAT Theory and Introduction
NAT Theory and Introduction
 Static NAT Configuration
Static NAT Configuration
 Dynamic NAT Configuration
Dynamic NAT Configuration
 PAT Configuration
PAT Configuration
Video 6 - EIGRP
 Introduction to EIGRP
Introduction to EIGRP
 Successors and Feasible Successors
Successors and Feasible Successors
 EIGRP vs. RIPv2
EIGRP vs. RIPv2
 Basic Configuration
Basic Configuration
 Wildcard Masks
Wildcard Masks
 Load Sharing (Equal and Unequal-cost)
Load Sharing (Equal and Unequal-cost)
 EIGRP, RIPv2, and Autosummarization
EIGRP, RIPv2, and Autosummarization
 Passive vs. Active Routes
Passive vs. Active Routes
 IPv6 Theory and Introduction
IPv6 Theory and Introduction
 Zero Compression and Leading Zero Compression
Zero Compression and Leading Zero Compression
 IPv6 Reserved Addresses
IPv6 Reserved Addresses
 The Autoconfiguration Process
The Autoconfiguration Process
 OSPF v3 Basics
OSPF v3 Basics
 Transition Strategies
Transition Strategies
 NAT Theory and Introduction
NAT Theory and Introduction
 Static NAT Configuration
Static NAT Configuration
 Dynamic NAT Configuration
Dynamic NAT Configuration
 PAT Configuration
PAT Configuration

Video 8 - VPNs and IPSec
 Definitions and Tunneling Protocols
Definitions and Tunneling Protocols
 Data Encryption Technologies
Data Encryption Technologies
 Key Encryption Schemes
Key Encryption Schemes
 IPSec, AH and ESP
IPSec, AH and ESP
 A VPN in Your Web Browser
A VPN in Your Web Browser
Video 9 - ACLs and Route Summarization
 ACL Login and the Implicit Deny
ACL Login and the Implicit Deny
 Standard ACLs and Remarks
Standard ACLs and Remarks
 "Host" and "Any"
"Host" and "Any"
 The Order of the Lines
The Order of the Lines
 Extended ACLs
Extended ACLs
 Named ACLs
Named ACLs
 Telnet Access, Placing ACLs, and Blocking Pings
Telnet Access, Placing ACLs, and Blocking Pings
 Dynamic and Time-Based ACLs
Dynamic and Time-Based ACLs
 Port Number Review
Port Number Review
 Route Summarization with RIP and EIGRP
Route Summarization with RIP and EIGRP
[E]. MCITP PAPER 05
MCITP PAPER 01
WINDOWS SERVER 2008 ACTIVE DIRECTORY TRAINING - COURSE OUTLINE
Introduction to the Course
Learn what's in the course, who you're instructor is, and what you can expect in the course. About the Instructor
About the Instructor What's Covered in this Course
What's Covered in this Course The Globomantics Scenario
The Globomantics Scenario
Class 2
What is Active Directory?
Get a foundation of what Active Directory is, what it can do, and why you want to use it in your network to make your life easier! What is Active Directory?
What is Active Directory? What is a Domain?
What is a Domain? What is a Server Role?
What is a Server Role? What is DNS?
What is DNS?
Class 3
Installing Server 2008 and Active Directory - The First Two Domain Controllers
Learn how to install Server 2008 from "bare metal", create a domain using Server 2008 by installing Active Directory Domain Services, and set up a second Domain Controller for redundancy. Building the Brain of the Globomantics Network
Building the Brain of the Globomantics Network Hardware Requirements
Hardware Requirements Server 2008 Editions
Server 2008 Editions Bare Metal Installation Process
Bare Metal Installation Process Windows Server 2008 Installation
Windows Server 2008 Installation Initial Configuration Task List
Initial Configuration Task List
 Installation of ADDS
Installation of ADDS Administrator Passwords
Administrator Passwords Renaming Default-First-Site-Name
Renaming Default-First-Site-Name Setting Up a Second Domain Controller
Setting Up a Second Domain Controller Replication Testing
Replication Testing
Setting up Remote Desktop on Your Personal Vista Client
Real administrators manage a network sitting down. It's so much easier to play World of Warcraft and Halo that way. Learn how to set up Remote Desktop shortcuts on a Vista client so you don't have to pause your game to trek into the server room every time somebody needs a password reset. The DC’s Are Up and Running… Now What?
The DC’s Are Up and Running… Now What? Renaming Vista Client Computer Name
Renaming Vista Client Computer Name Joining Vista Client to Globomantics Domain
Joining Vista Client to Globomantics Domain Recording Transactions
Recording Transactions Troubleshooting Connection Problem
Troubleshooting Connection Problem
 Troubleshooting RPC Server Error
Troubleshooting RPC Server Error Why Remote Desktop is Just Great
Why Remote Desktop is Just Great Setting Up Remote Desktop Shortcut
Setting Up Remote Desktop Shortcut
Class 5
Creating OU's, Users, Computers and Groups in Active Directory
Create Organizational Units to keep your Active Directory organized, making your IT life easier in the long term. Learn the secrets of creating a lot of users quickly and easily using scripts. *Bonus* Coach's Active Directory Toolbox File: Coach's Mass User Creation Script Builder!!!! Plus, a simple batch script to create single users all day long! The DC’s Are Up and Running – Now What? – Part 2
The DC’s Are Up and Running – Now What? – Part 2 What’s an OU Again?
What’s an OU Again? Creating an Organizational Unit
Creating an Organizational Unit Deleting on OU
Deleting on OU Creating User Accounts
Creating User Accounts Introducing DSADD
Introducing DSADD Creating Users Using a Script
Creating Users Using a Script Creating Users Using Excel
Creating Users Using Excel Creating Computer Accounts
Creating Computer Accounts Diff. Between OUs & Groups
Diff. Between OUs & Groups Creating Groups in AD
Creating Groups in AD Adding Users and Computers into Groups
Adding Users and Computers into Groups
Class 6
Setting up Share Folders and Printers, Mapping Drives, and Creating Permissions
Create Shared Folders so users can easily get to stuff on your network. Share Network printers. Learn the arcane secrets of NTFS and Share level Permissions, and Delegation Security Filtering! Become a wizard at giving only the people you want to have access to stuff! Rule your IT Kingdom with an iron fist and fear or with a soft heart and love--you decide! Setting Up a Member Server
Setting Up a Member Server File Server Partitions
File Server Partitions Creating Shared Folders
Creating Shared Folders Share Level Permissions
Share Level Permissions Using Share and Storage Management MMC
Using Share and Storage Management MMC Using Windows Explorer to Create Shared Folders
Using Windows Explorer to Create Shared Folders Testing Shared Folders
Testing Shared Folders Groups and Permissions: Good Idea that Could Go Very Wrong
Groups and Permissions: Good Idea that Could Go Very Wrong Making a Group a Member of Another Group
Making a Group a Member of Another Group Share Level vs. NTFS
Share Level vs. NTFS
 What is Inheritance
What is Inheritance Creating NTFS Permissions
Creating NTFS Permissions Checking NTFS Permissions
Checking NTFS Permissions Rules for Share Level and NTFS Permissions
Rules for Share Level and NTFS Permissions Moving Folders
Moving Folders Mapping a Shared Drive
Mapping a Shared Drive Checking Group Memberships
Checking Group Memberships Creating and Sharing Printers
Creating and Sharing Printers Adding a Printer
Adding a Printer What Globomantics.com Looks Like Now
What Globomantics.com Looks Like Now
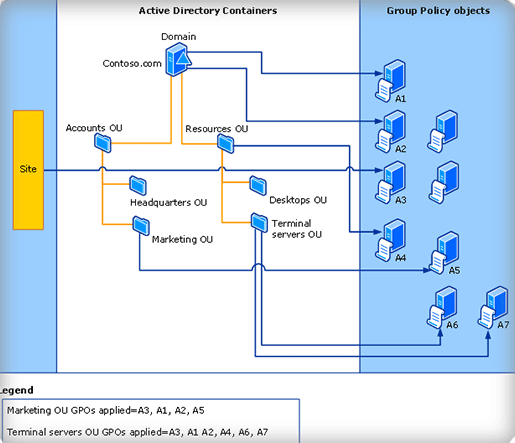
Group Policy Objects
Learn how to lock down your desktop machines with Group Policy. Keep users from screwing stuff up, installing World of Warcraft, and from stealing data by using USB drives! The power is yours! Group Policy Objects
Group Policy Objects Group Policy Management Console
Group Policy Management Console Default Domain Policy
Default Domain Policy Local Vs. Domain Policy
Local Vs. Domain Policy Configuring Domain Level Policy
Configuring Domain Level Policy Linking GPOs
Linking GPOs
 GPO’s Processing Order
GPO’s Processing Order Setting Up Coach’s Favorite Four Policies
Setting Up Coach’s Favorite Four Policies Desktop Wallpaper Policy
Desktop Wallpaper Policy Preventing Users from Installing Software
Preventing Users from Installing Software Removable Storage Policy
Removable Storage Policy Testing Our Policies
Testing Our Policies
Class 8
Security Filtering and Setting Up OUs for Better Group Policy Implementation
When Group Policy Attacks! Does your boss insist on having absolute control over a personal laptop? Then buy our product and learn how to allow your boss absolute freedom over his/her personal machine so you can continually fix it, and keep your job forever! (Or until something higher-paying comes along!) A Little Reorganization: Option 1, 2 or 3?
A Little Reorganization: Option 1, 2 or 3? Using a Combination of Techniques
Using a Combination of Techniques Reorganizing Users & Computers
Reorganizing Users & Computers Running “gpupdate” Command
Running “gpupdate” Command Checking DCs Replication
Checking DCs Replication Testing Our Reorganized Active Directory
Testing Our Reorganized Active Directory
Class 9
Computer Policies and Preferences
Learn the magic of Loopback processing, what "hoteling" means, and how you can lockdown machines no matter who's using them! Quick Review of Our Network
Quick Review of Our Network Policy Settings to Computer Lockdown
Policy Settings to Computer Lockdown Reorganizing Computer OUs
Reorganizing Computer OUs Creating Computer GPOs
Creating Computer GPOs Loopback Processing
Loopback Processing Group Policy Intervals
Group Policy Intervals Testing Computer GPOs
Testing Computer GPOs Mapping Network Drives with Preferences
Mapping Network Drives with Preferences Testing Preferences – Mapped Drives
Testing Preferences – Mapped Drives
Using GPOs to Install Software
Do you want to be able to sit at your desk all day long and install software by just clicking your mouse? Then pick up this course and learn how to install, upgrade, and uninstall software and not even have to get your butt out of your nice cushy office chair! You are Here: a Quick Look at What We’ve Built
You are Here: a Quick Look at What We’ve Built Options for Installing Software
Options for Installing Software What You Need for a Software Installing GPO
What You Need for a Software Installing GPO Steps for Creating GPO for Software Installation
Steps for Creating GPO for Software Installation Creating a Shared Folder for Foxit.msi Package
Creating a Shared Folder for Foxit.msi Package Creating and Linking a New GPO to the NYComputers OU
Creating and Linking a New GPO to the NYComputers OU Testing Our New GPO Software Installation
Testing Our New GPO Software Installation Default Domain Policy Settings
Default Domain Policy Settings
Class 11
Domain and Fine-Grained Password Policies
Are you kidding? You forgot your password again? Learn how to provide multiple password policies using Server 2008's brand new Fine Grained Password Policy Objects! That's right, you too can lessen the security of your network so your boss can use the name of his or her favorite horse as his/her password and not have to worry about all that security stuff! The Default Domain Password Policy
The Default Domain Password Policy Account Lockout Policy
Account Lockout Policy Letting Your Boss Use Whatever Password He/She Wants
Letting Your Boss Use Whatever Password He/She Wants Password Management
Password Management Server 2008 Functional Level
Server 2008 Functional Level
Class 12
Providing Permissions to an Account for Administrative Tasks
Feeling tired and overworked? Are you ready to let someone else do the busy work of resetting passwords and the like? Then you need Class 12! Pass off some of your responsibility to some other unsuspecting IT staffer and make them take the calls from your users! You'll have much more time to play Halo! Giving Someone Else the Ability to Reset Passwords
Giving Someone Else the Ability to Reset Passwords Additional Built-In Groups in OUs
Additional Built-In Groups in OUs Delegation of Control Wizard
Delegation of Control Wizard Additional Built-In Groups Demo
Additional Built-In Groups Demo Installing RSAT to a Vista Client for Easy Server Management
Installing RSAT to a Vista Client for Easy Server Management Configuring RSAT for Vista
Configuring RSAT for Vista

Windows Server Backup, WBADMIN, and NTDSUTIL
If you don't know how to create basic backups, there's a chance your network will go down in flames and there will be nothing you'll be able to do about it. Millions of dollars of lost data! Just think of the chaos that will reign if your boss can't find the annual TPS report! You need to watch this Class and you never know; you might even become the hero, save the princess, and get a parade thrown in your honor! Prevention
Prevention WBADMIN – Stronger Tools and More Options
WBADMIN – Stronger Tools and More Options NTDSUTIL – Super-Powered Utility for Lots of Operations
NTDSUTIL – Super-Powered Utility for Lots of Operations The Globomantics Backup Strategy
The Globomantics Backup Strategy Installing Windows Server Backup on DC2
Installing Windows Server Backup on DC2
 Windows Server Backup Setup and Configuration
Windows Server Backup Setup and Configuration Selecting Backup Once Wizard
Selecting Backup Once Wizard System State Backup with WBADMIN
System State Backup with WBADMIN Creating Install for Media (IFM) Media
Creating Install for Media (IFM) Media
Class 14
Moving Operations Masters and Adding a DC with IFM
Give your network some flexibility by learning the secret of multiple Domain Controllers having different FSMO's! A Little Future Planning to Prevent Major Problems
A Little Future Planning to Prevent Major Problems What Are Operations Masters?
What Are Operations Masters? Restructuring the Globomantics DCs a Bit
Restructuring the Globomantics DCs a Bit Moving PDC Emulator and RID to DC2
Moving PDC Emulator and RID to DC2 Building DC3 with IFM Media
Building DC3 with IFM Media Verifying DC3 Configuration
Verifying DC3 Configuration
Class 15
Computer Policies and Preferences
Learn the magic of Loopback processing, what "hoteling" means, and how you can lockdown machines no matter who's using them! Quick Review of Our Network
Quick Review of Our Network Policy Settings to Computer Lockdown
Policy Settings to Computer Lockdown Reorganizing Computer OUs
Reorganizing Computer OUs Creating Computer GPOs
Creating Computer GPOs Loopback Processing
Loopback Processing Group Policy Intervals
Group Policy Intervals Testing Computer GPOs
Testing Computer GPOs Mapping Network Drives with Preferences
Mapping Network Drives with Preferences Testing Preferences – Mapped Drives
Testing Preferences – Mapped Drives
Adding a Child Domain and Configuring Replication
Hey, it's time to expand! Learn how to create a new Child Domain for a new location so you can eventually pass off the responsibility for it to another victim--I mean administrator! Before We Begin
Before We Begin Creating Chicago Site in AD
Creating Chicago Site in AD Creating Subnet for Chicago Office
Creating Subnet for Chicago Office
 Installing Domain Controller for Chicago
Installing Domain Controller for Chicago Configuring Replication
Configuring Replication
Class 17
Creating Universal Groups and the AGUDLP Strategy
Users in Chicago need access to stuff in New York! What are we going to do? Using Universal Groups and a strategy called AGUDLP, we can provide access to stuff that's 790 miles away over the network! Time for Some More Users!
Time for Some More Users! Organizing Users into Groups
Organizing Users into Groups The Types of Groups
The Types of Groups Setting Up Your Groups for Access Between Domains
Setting Up Your Groups for Access Between Domains  AGUDLP Setup
AGUDLP Setup Checking Our Settings
Checking Our Settings Making Sure Your Users Can Log in Anywhere in Your Enterprise
Making Sure Your Users Can Log in Anywhere in Your Enterprise Turning on Universal Group Membership Cashing
Turning on Universal Group Membership Cashing
Class 18
Building a Read-Only Domain Controller
Do you need a full Domain Controller for a branch office of 5 people? No, you really don't. Using Windows Server Core and the Read-Only Domain Controller feature in Windows Server 2008, you can create an great experience for your remote users that's more secure and cheaper to implement! Dallas OU and Site Structure
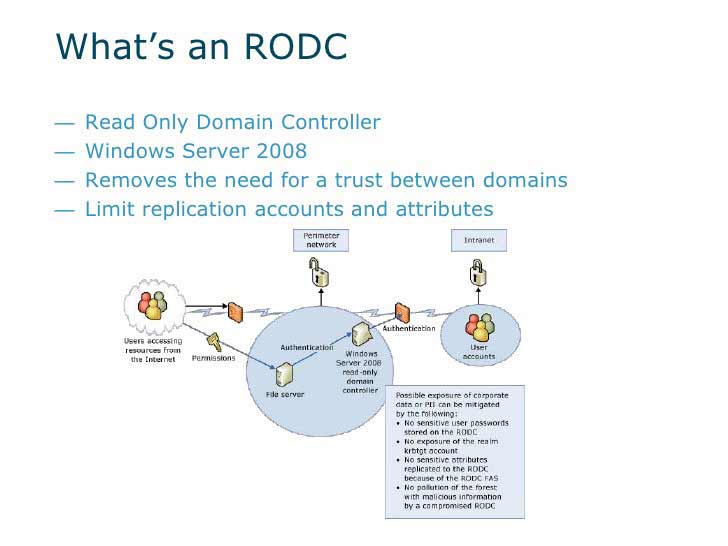
Dallas OU and Site Structure What is a Read-Only Domain Controller?
What is a Read-Only Domain Controller? Building RODC for Dallas
Building RODC for Dallas Server Core Installation
Server Core Installation Running dcpormo on Server Coreli>
Running dcpormo on Server Coreli>
 Verifying Our Installation
Verifying Our Installation Configuring RODC
Configuring RODC Setting Up Users
Setting Up Users What We’ve Built so Far…
What We’ve Built so Far…

Restoring OUs and User Accounts
That new third shift IT guy we just hired deleted the entire New York Ops dept! What do we do? Since we were smart and created backups in Class 13, we can get back only the stuff we want using NTDSUTIL. There will be no need to recreate User Accounts -- but tell the boss that it'll take hours and hours to fix the problem, and then you can spend the time that you were going to take up recreating those OU's and Accounts to play a little Bejeweled. The Two Types of Restorations
The Two Types of Restorations Authoritative Restore
Authoritative Restore
 Checking Our Recovery Files and Objects
Checking Our Recovery Files and Objects How to Put Resurrected Users Back Into Groups Using Backlinks?
How to Put Resurrected Users Back Into Groups Using Backlinks?
Class 20
Strategies for Recreating a Domain Controller
It is inevitable. You will eventually face a cataclysmic meltdown of a Domain Controller. If you've applied the principles in the previous Classs, restoring and recreated DC's doesn't have to be tough. Coach will show you how! Seizing Operations Masters for Quick Restoration of Functionality
Seizing Operations Masters for Quick Restoration of Functionality Possible Solutions for Restoring Domain Controllers
Possible Solutions for Restoring Domain Controllers
Class 21
Upgrading a Server 2003 Machine to Server 2008
So what about all those Server 2003 machines out there? In this Class you'll learn a little secret to upgrading your DC's to Server 2008, and it won't take much time at all. Hank Just Bought a Company … in Tokyo!
Hank Just Bought a Company … in Tokyo! Advantages of the Server 2008 Domain Functional Level
Advantages of the Server 2008 Domain Functional Level The Upgrade Process
The Upgrade Process Preparing Tokyo DC for Upgrade
Preparing Tokyo DC for Upgrade Upgrading Tokyo DC to Windows Server 2008
Upgrading Tokyo DC to Windows Server 2008
Connecting Two Active Directory Networks
In this Class you'll learn how to connect two Active Directory Forests together. There's two options: Active Directory Federation Services or Trusts? Which one will it be? Which option is easiest? You have to watch to find out! Our Two Options to Connect Tokyo and New Yorkli>
Our Two Options to Connect Tokyo and New Yorkli>
 What You Need for a Trust
What You Need for a Trust Trust Directions
Trust Directions The Globomantics/Verde Petra Solution: Trusts
The Globomantics/Verde Petra Solution: Trusts
 Creating a Stub Zone
Creating a Stub Zone Raising Forest Functional Level
Raising Forest Functional Level Creating Trusts
Creating Trusts Checking and Updating User Permissions
Checking and Updating User Permissions
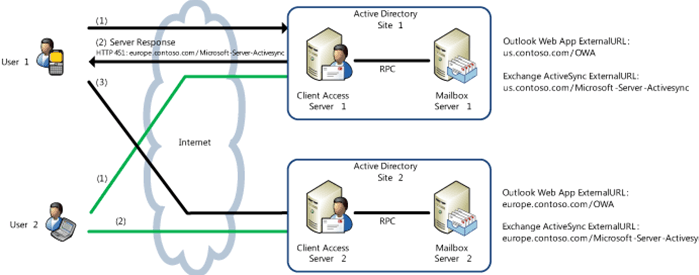
Class 23
Certification: It's Really Not That Scary
Are you thinking about taking the 70-640, Configuring Windows Server 2008 Active Directory Exam so you too can get a shiny new Microsoft Certified Technology Specialist (MCTS) in Active Directory, Configuring? If so, you'll want to watch this Class to know how to prepare for the big day. PLUS: Coach shares his secrets to passing the exams! The New Generation of Server 2008 Certifications
The New Generation of Server 2008 Certifications The Upgrade Paths for MCSA’s/MCSE’s
The Upgrade Paths for MCSA’s/MCSE’s How to Sign Up for a Microsoft Exam
How to Sign Up for a Microsoft Exam 70-640 Exam Prep Tips
70-640 Exam Prep Tips
Class 24
Domain Name Service
Without DNS, your Domain Controllers are really expensive paperweights. In this exam prep Class, you'll pick up some additional vocabulary and core concepts of DNS. A Quick Overview of DNS
A Quick Overview of DNS What are DNS Zones Really?
What are DNS Zones Really? The Different Kinds of DNS Records
The Different Kinds of DNS Records Forward Lookup Zones
Forward Lookup Zones Reverse Lookup Zones
Reverse Lookup Zones Conditional Forwarders
Conditional Forwarders Forwarders and Root Hints
Forwarders and Root Hints Global Name Zones
Global Name Zones

Active Directory Certificate Services 101
Now that Certificate Services has stronger integration with Active Directory, it's now on the 70-640 exam. This exam prep Class will give you a quick foundation and the important jargon for Certificate Services. Let’s Talk Security
Let’s Talk Security Keys and Certificates
Keys and Certificates
 Your Certificate Has Been Revoked
Your Certificate Has Been Revoked
Class 26
Lightweight Directory Services 101
In this exam prep Class, you'll learn about the AD LDS Role, and why you might need it if you have network applications that require LDAP. What is AD LDS?
What is AD LDS? What Might it Look Like on a Network?
What Might it Look Like on a Network? What is an Instance of AD LDS?
What is an Instance of AD LDS?
Class 27
Rights Management Services 101
In our final exam prep Class for this series, you'll learn about a new Role in Server 2008 that allows you to lock down the data in your network in an easy to implement fashion. Make the users do the work! What is Rights Management?
What is Rights Management? Some Additional Notes About RMS
Some Additional Notes About RMS
MCITP PAPER 02
Windows Server 2008 Network Infrastructure Training - Course Outline
Introduction to the Course
Learn what’s in the course and who you’re instructor is. About the Instructor
About the Instructor What's Covered in this Course
What's Covered in this Course The Globomantics Scenario
The Globomantics Scenario What You Will Need
What You Will Need
Class 2
Configuring DHCP
Learn how to simplify the process of assigning IP addresses to the computers on your network. Introduction to DHCP
Introduction to DHCP
 How Does DHCP Work
How Does DHCP Work How to Configuring DHCP in Windows Server 2008?
How to Configuring DHCP in Windows Server 2008? Authorizing DHCP
Authorizing DHCP Creating Scopes
Creating Scopes Configuring Scope Options
Configuring Scope Options Address Leases
Address Leases Reservations
Reservations Using DHCP in a Routed Network
Using DHCP in a Routed Network How Does DHCP Relay Agent Work?
How Does DHCP Relay Agent Work? How to Configuring a DHCP Relay Agent in Windows Server 2008
How to Configuring a DHCP Relay Agent in Windows Server 2008
Class 3
Managing DHCP
Learn how to keep your DHCP infrastructure properly functioning. Add and Remove Bindings
Add and Remove Bindings
 Location of Database
Location of Database Backup & Restore
Backup & Restore DHCP Service
DHCP Service DHCP Management Permissions
DHCP Management Permissions Statistics
Statistics Scope Reconciliation
Scope Reconciliation Audit Logging
Audit Logging Conflict Detection
Conflict Detection Integration with DNS and NAP
Integration with DNS and NAP Performance Counters
Performance Counters
Setting Up Routing
Learn how to make your networks talk to each other. What is a Router?
What is a Router?
 How to Use Server 2008 as a Router
How to Use Server 2008 as a Router Routing Table
Routing Table Adding Static Entry to a Routing Table
Adding Static Entry to a Routing Table Inbound and Outbound Filters
Inbound and Outbound Filters Static vs. Dynamic Routing
Static vs. Dynamic Routing Dynamic Routing Protocols: RIP & OSPF
Dynamic Routing Protocols: RIP & OSPF How RIP Works in Server 2008
How RIP Works in Server 2008
Class 5
Configuring DNS
Learn how to set-up your network so users can access computers using common names. Introduction to DNS
Introduction to DNS  Installing the DNS Server Role in Windows Server 2008
Installing the DNS Server Role in Windows Server 2008 What is a Domain Namespace?
What is a Domain Namespace? What is a DNS Query?
What is a DNS Query? How Queries Work
How Queries Work What is a Forwarder?
What is a Forwarder? Setting Up Standard DNS Forwarders in Windows Server 2008
Setting Up Standard DNS Forwarders in Windows Server 2008 Setting Up Conditional DNS Forwarders in Windows Server 2008
Setting Up Conditional DNS Forwarders in Windows Server 2008 How Caching Works
How Caching Works Clearing the DNS Cache
Clearing the DNS Cache
 What is a DNS Zone?
What is a DNS Zone? Zone Types
Zone Types
 Stub Zones
Stub Zones Active Directory Integrated Zones
Active Directory Integrated Zones Forward and Reverse Lookup
Forward and Reverse Lookup Dynamic Updates
Dynamic Updates Configuring a DNS Zone
Configuring a DNS Zone Creating Stub Zones
Creating Stub Zones DNS Records
DNS Records DNS Zone Transfers
DNS Zone Transfers Configuring Resource Records and Zone Transfers
Configuring Resource Records and Zone Transfers Zone Transfer Issues
Zone Transfer Issues
Class 6
Managing DNS
Know how to keep your DNS infrastructure properly functioning. What is Time to Live? (TTL)
What is Time to Live? (TTL) What is Aging and Scavenging?
What is Aging and Scavenging? Setting the TTL Value and the Aging and Scavenging Parameters
Setting the TTL Value and the Aging and Scavenging Parameters Testing DNS Queries
Testing DNS Queries nslookup
nslookup dnscommand
dnscommand Performance Monitor
Performance Monitor DNS Event Logs
DNS Event Logs DNS Debug Logging
DNS Debug Logging
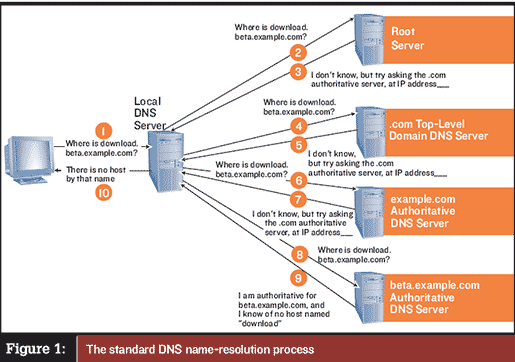
Name Resolution
This Class takes Name Resolution beyond what you learned in Class 5 and gives a complete understanding of how to convert names that are easily recognizable to humans into IP addresses. What are Host and NetBIOS Names?
What are Host and NetBIOS Names?
 How Are Names Resolved?
How Are Names Resolved? Hosts & LMHosts Files / DNS & WINS Servers
Hosts & LMHosts Files / DNS & WINS Servers DNS & WINS Servers
DNS & WINS Servers hostname & nbtstat Commands
hostname & nbtstat Commands
 Client Configuration
Client Configuration Troubleshooting Name Resolution
Troubleshooting Name Resolution DNS Cache and Host File
DNS Cache and Host File GlobalNames Zone
GlobalNames Zone WINS Lookup and GlobalNames Zone Demo
WINS Lookup and GlobalNames Zone Demo
Class 8
Securing Data
Learn how to control access to your data and keep it safe. NTFS Permissions
NTFS Permissions
 Assigning NTFS Permission
Assigning NTFS Permission Special NTFS Permissions
Special NTFS Permissions Inheritable Permissions
Inheritable Permissions Examples - Effective User Permissions
Examples - Effective User Permissions Creating Users & Groups
Creating Users & Groups Demo - Effective User Permissions
Demo - Effective User Permissions Encrypting File System (EFS)
Encrypting File System (EFS) Cryptography
Cryptography Public Key Encryption
Public Key Encryption How Does EFS Work?
How Does EFS Work? Enabling EFS
Enabling EFS
Class 9
Sharing Data
Learn how to make files and folders accessible to users across your network. Sharing Folders
Sharing Folders
 Installing File Service Role
Installing File Service Role Sharing Using Provision a Share Folder Wizard
Sharing Using Provision a Share Folder Wizard Accessing Shared Folder
Accessing Shared Folder Disk Quotas
Disk Quotas Setting Disk Quotas Using Group Policy
Setting Disk Quotas Using Group Policy Quota Management Utility
Quota Management Utility Offline Files
Offline Files Distributed File System (DFS)
Distributed File System (DFS) Creating Replica on a Different Server
Creating Replica on a Different Server Raising Domain & Forest Functional Level
Raising Domain & Forest Functional Level
Configuring Print Services
Learn how to make printers easily available to your users. Installing a Printer
Installing a Printer  Sharing a Printer
Sharing a Printer Installing Print Services Role
Installing Print Services Role Using Print Management Snap-In
Using Print Management Snap-In Configuring Print Permissions
Configuring Print Permissions Printer Priorities and Scheduling
Printer Priorities and Scheduling Printer Pooling
Printer Pooling Setting Up Printer Pooling on Server 2008
Setting Up Printer Pooling on Server 2008 Managing Drivers
Managing Drivers Troubleshooting Printers
Troubleshooting Printers Restarting Printer Spooler Service
Restarting Printer Spooler Service

Class 11
Windows Server Update Services
Learn how to simplify the process of keeping all of your computers up to date. What Is WSUS?
What Is WSUS?
 Why Use WSUS?
Why Use WSUS? Installing Necessary Services
Installing Necessary Services Downloading and Installing WSUS
Downloading and Installing WSUS Configuring WSUS Server Options
Configuring WSUS Server Options Computer Groups and Server-Side Targeting
Computer Groups and Server-Side Targeting Using Group Policy and Client-Side Targeting
Using Group Policy and Client-Side Targeting  How to Approve Updates
How to Approve Updates
Class 12
Backup and Recovery
Learn how to protect important data from being lost by human error or computer malfunction. How to Configure the Shadow Copy Service
How to Configure the Shadow Copy Service
 Recovering Data Using Shadow Copy
Recovering Data Using Shadow Copy Installing the Windows Server Backup Feature
Installing the Windows Server Backup Feature Creating a Backup Volume
Creating a Backup Volume Scheduling Backups
Scheduling Backups Recovering Data
Recovering Data Complete System Recovery
Complete System Recovery Additional Backup Tips
Additional Backup Tips

Monitoring Windows Server 2008
Understand the common tools used to monitor your servers and keep them running efficiently. Task Manager
Task Manager
 Event Viewer
Event Viewer Performance Monitor
Performance Monitor Reliability Monitor
Reliability Monitor Data Collector Sets
Data Collector Sets
Class 14
Configuring Remote Access
Learn how to let users safely connect from outside your network. Installing the RRAS Component
Installing the RRAS Component
 Configuring RRAS
Configuring RRAS How to Configure a Client to Connect
How to Configure a Client to Connect Making a Connection
Making a Connection Manually Controlling Connections
Manually Controlling Connections Creating a Network Policy
Creating a Network Policy Network Policy Order
Network Policy Order Testing Our New Network Policy
Testing Our New Network Policy Configuring RRAS - True VPN Setup
Configuring RRAS - True VPN Setup What is RADIUS?
What is RADIUS?
Class 15
Wireless Networks
Learn how to let users safely connect without using cables. Is Wireless Good or Bad?
Is Wireless Good or Bad?
 Wireless Networking Standards
Wireless Networking Standards Wireless Security (Maybe)
Wireless Security (Maybe) Connecting to a Wireless Network
Connecting to a Wireless Network Setting Up Security on a Router
Setting Up Security on a Router
Windows Firewall
Learn how to keep control over what data enters and exits your network. Why Do We Need a Firewall?
Why Do We Need a Firewall?
 Windows Firewall in Server 2008
Windows Firewall in Server 2008 Firewall Profiles
Firewall Profiles
 Creating a New Firewall Rule
Creating a New Firewall Rule
 Creating a Program Outbound Rule
Creating a Program Outbound Rule
 Configuring with Group Policy
Configuring with Group Policy
Class 17
Securing Network Traffic with IPSec
Learn how to protect data from being compromised while travelling on a network. What is IPSec?
What is IPSec?
 IPSec Protocols
IPSec Protocols
 Tunnel Mode vs. Transport Mode
Tunnel Mode vs. Transport Mode
 Authentication Methods
Authentication Methods
 Configuring IPSec in Server 2008
Configuring IPSec in Server 2008
 Creating New IPSec Policy
Creating New IPSec Policy
 Getting IPSec to Work
Getting IPSec to Work
 Using Connection Security Rules
Using Connection Security Rules
Class 18
Network Access Protection
Learn how to create rules and stipulations to maintain control over network communications. What is NAP?
What is NAP?
 NAP Enforcement Types
NAP Enforcement Types
 System Health Agents (SHAs) and System Health Validators (SHVs)
System Health Agents (SHAs) and System Health Validators (SHVs)
 Health Requirement Policies
Health Requirement Policies
 Installing Necessary Roles: DHCP Role and Network Policy and Access Services Role
Installing Necessary Roles: DHCP Role and Network Policy and Access Services Role
 Installing and Configuring NAP: DHCP Enforcement
Installing and Configuring NAP: DHCP Enforcement
 NAP Client Configuration
NAP Client Configuration
 Testing Our Client for NAP Enforcement
Testing Our Client for NAP Enforcement

Certification
Are you thinking about taking the 70-642, Configuring Windows Server 2008 Network Infrastructure Exam? If so, you'll want to watch this Class to know how to prepare for the big day with Ed’s secrets to passing the exams! The New Generation of Server 2008 Certifications
The New Generation of Server 2008 Certifications
 The Upgrade Paths for MCSA’s/MCSE’s
The Upgrade Paths for MCSA’s/MCSE’s How to Sign Up for a Microsoft Exam
How to Sign Up for a Microsoft Exam 70-642 Exam Prep Tips
70-642 Exam Prep Tips
MCITP PAPER 03
Windows Server 2008 Server Administrator Training - Course Outline

Windows Server 2008 Installation and Upgrade
Learn about the different versions of Windows Server 2008 and dive right into installing Windows Server 2008 from scratch. Plus, we'll install the Active Directory Domain Services role and perform an upgrade from Windows Server 2003 to Server 2008. Windows Server 2008 Versions
Windows Server 2008 Versions Standard Edition
Standard Edition Enterprise Edition
Enterprise Edition Datacenter Edition
Datacenter Edition Windows Web Server 2008
Windows Web Server 2008 Itanium-Based Systems
Itanium-Based Systems Installing Windows Server 2008 from Scratch
Installing Windows Server 2008 from Scratch Initial Configuration Tasks (ICT)
Initial Configuration Tasks (ICT)
 Downloading and Installing Updates
Downloading and Installing Updates Adding Active Directory Role
Adding Active Directory Role Creating Active Directory Domain Controller
Creating Active Directory Domain Controller Finishing Up ICT List
Finishing Up ICT List Server Manager Overview
Server Manager Overview Globomantics Network Diagram
Globomantics Network Diagram Upgrading Server 2003 to Server 2008
Upgrading Server 2003 to Server 2008
Class 2
Simplifying Installations Using Windows Deployment Services (WDS)
Learn to install the DHCP role, install and configure WDS, install and implement Windows Automated Installation Kit (WIAK), and use Multicast Transmission to perform unattended installastions of Windows Server 2008. Getting Ready for WDS
Getting Ready for WDS Installing DHCP Role
Installing DHCP Role Installing WDS Role
Installing WDS Role Configuring WDS
Configuring WDS Adding Image to WDS
Adding Image to WDS WDS Properties
WDS Properties Setting Up Multicast Transmission
Setting Up Multicast Transmission Deploying Using Multicast Transmission
Deploying Using Multicast Transmission Finishing Up Deployment Manually
Finishing Up Deployment Manually Installing Automated Installation Kit (AIK)
Installing Automated Installation Kit (AIK) Creating an Answer File with Windows System Image Master (SIM) Tool
Creating an Answer File with Windows System Image Master (SIM) Tool Running Unattended Installation
Running Unattended Installation Where to get Windows AIK
Where to get Windows AIK
Class 3
Installing Windows Server 2008 Server Core
Discover what Server Core is and learn to install and configure Server Core. Plus, we will use Remote Server Administration Tools (RSAT) and Remote Desktop to remotely manage our Server Core. What is Server Core?
What is Server Core? When Should I Use Server Core?
When Should I Use Server Core? Globomantics Scenario
Globomantics Scenario Installing Windows Server 2008 Server Core
Installing Windows Server 2008 Server Core Installing Core Configurator Utility
Installing Core Configurator Utility Setting Up Windows Server Core with Core Configurator
Setting Up Windows Server Core with Core Configurator Remote Management
Remote Management Downloading and Installing RSAT
Downloading and Installing RSAT Setting Up RSAT
Setting Up RSAT Setting Up Secondary DNS Server on Server Core
Setting Up Secondary DNS Server on Server Core Remote Desktop Management
Remote Desktop Management
Deploying Read Only Domain Controllers (RODC)
Install RODC in our scenario's branch office and learn to configure a password replication policy. Plus, discover how to use Administrative Role Separation. RODC Benefits
RODC Benefits Globomantics Network
Globomantics Network Installing Read Only Domain Controller (RODC)
Installing Read Only Domain Controller (RODC) Testing Replication Between a DC and RODC
Testing Replication Between a DC and RODC Configuring a Password Replication Policy
Configuring a Password Replication Policy Administrative Role Separation
Administrative Role Separation
Class 5
Virtualization
Learn the benefits of using virtualization and discover the differences and similarities between available virtualization products. Plus, work through virtualization examples and find out when virtualization may be necessary and when you may run into potential virtualization issues. What is Virtualization?
What is Virtualization? Benefits of Using Virtualization
Benefits of Using Virtualization Virtualization Products
Virtualization Products Virtualization Examples
Virtualization Examples Potential Issues
Potential Issues
Class 6
Using Group Policy to Simplify Network Administration
Learn to create, link, edit, and view Group Policy Objects (GPOs) and GPO Settings using the Group Policy Object Management Tool. Plus, discover how to implement new features exclusive to Windows Server 2008 including Starter GPOs and Password Setting Objects (PSO). Active Directory Review
Active Directory Review Globomantics Network - Logical Structure
Globomantics Network - Logical Structure Active Directory Objects
Active Directory Objects Active Directory – Trusts
Active Directory – Trusts What is a GPO?
What is a GPO? Globomantics Scenario
Globomantics Scenario Group Policy Management Tool - Create and Link GPOs
Group Policy Management Tool - Create and Link GPOs Edit “Block Removable Device Installation” GPO Settings
Edit “Block Removable Device Installation” GPO Settings Edit “Disable Add/Remove Programs” GPO Settings
Edit “Disable Add/Remove Programs” GPO Settings
 Edit “Create Shortcut” GPO Settings
Edit “Create Shortcut” GPO Settings Starter GPOs
Starter GPOs How Do GPOs Get Applied?
How Do GPOs Get Applied? Exception to the Rules
Exception to the Rules Globomantics Scenario
Globomantics Scenario Enforced and Security Filtering
Enforced and Security Filtering Block Inheritance
Block Inheritance Group Policy Modeling and Results Wizards
Group Policy Modeling and Results Wizards Password Setting Objects (PSO)
Password Setting Objects (PSO)

Delegation of Control
Learn about the different types of permissions and configure those permissions using the Delegation of Control Wizard. Plus, we will create a custome Microsoft Management Console (MMC). Different Types of Permissions
Different Types of Permissions Configuring Permissions
Configuring Permissions Globomantics Scenario
Globomantics Scenario Setting Permissions in Active Directory
Setting Permissions in Active Directory Delegation of Control Wizard
Delegation of Control Wizard Creating Custom MMC
Creating Custom MMC
Class 8
Setting Up a File and Print Server
Learn how to install the file and print service roles and set up disk quotas using the File System Resource Manager (FSRM). Plus, discover how to install and share a printer and troubleshoot printer problems. Globomantics Scenario
Globomantics Scenario Installing File Services Role
Installing File Services Role NTFS File and Folder Permissions
NTFS File and Folder Permissions What are Inherited Permissions?
What are Inherited Permissions? Folder Redirection Steps
Folder Redirection Steps Setting up Disk Quotas
Setting up Disk Quotas Using File Server Resource Manager to Setup Disk Quotas
Using File Server Resource Manager to Setup Disk Quotas Checking Redirection Settings
Checking Redirection Settings Installing Print Services Role
Installing Print Services Role Installing and Sharing a Printer
Installing and Sharing a Printer Printer Permissions
Printer Permissions Installing Printer on a Client
Installing Printer on a Client Troubleshooting Printers
Troubleshooting Printers NTFS Permissions Review – AGDLP
NTFS Permissions Review – AGDLP
Class 9
Data Provisioning
Learn to share a folder, set permissions for that share, and configure caching on shared folders to allow offline access. Plus, increase fault tolerance by creating a Distributed File System Namespace (DFS) and by configuring DFS replication. Globomantics Scenario
Globomantics Scenario Creating a Share
Creating a Share Managing Permissions to Share a Folder
Managing Permissions to Share a Folder Testing Our Share on a Client Machine
Testing Our Share on a Client Machine Configuring Caching
Configuring Caching Accessing a Shared Folder Offline
Accessing a Shared Folder Offline Installing DFS Role Service and Creating a DFS Namespace
Installing DFS Role Service and Creating a DFS Namespace Accessing DFS Share
Accessing DFS Share Configuring DFS Replication
Configuring DFS Replication Testing Replication
Testing Replication DFS Management - Configuring Fault Tolerance
DFS Management - Configuring Fault Tolerance Testing Fault Tolerance
Testing Fault Tolerance
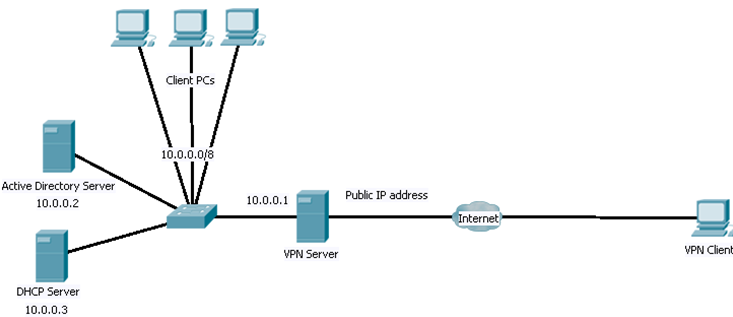
Setting Up a VPN Server
 What is a VPN?
What is a VPN? Supported Authentication Protocols
Supported Authentication Protocols Choosing a VPN Protocol
Choosing a VPN Protocol Globomantics Scenario
Globomantics Scenario Installing Remote Access Service
Installing Remote Access Service Configuring Routing & Remote Access Server to Support VPN Connectivity
Configuring Routing & Remote Access Server to Support VPN Connectivity
 DHCP Relay Agent Setupli>
DHCP Relay Agent Setupli>
 Configuring DHCP Options
Configuring DHCP Options Authentication Protocols
Authentication Protocols Creating VPN Connection for a Client
Creating VPN Connection for a Client Managing VPN Users
Managing VPN Users
Class 11
Network Policy Server
 What is a RADIUS?
What is a RADIUS? Globomantics Scenario
Globomantics Scenario Installing Network Policy Server (NPS) Role
Installing Network Policy Server (NPS) Role Configuring NPS Server as RADIUS Server
Configuring NPS Server as RADIUS Server Configuring Remote Access Server as RADIUS Client
Configuring Remote Access Server as RADIUS Client Creating a Network Policy
Creating a Network Policy Testing the Network Policy
Testing the Network Policy
Class 12
Using Group Policy to Simplify Network Administration
 What is WSUS?
What is WSUS? Why us WSUS?
Why us WSUS? Where Can I Get WSUS?
Where Can I Get WSUS? Single Server
Single Server Independent
Independent Autonomous Mode
Autonomous Mode Replica Mode
Replica Mode Disconnected
Disconnected Globomantics Scenario
Globomantics Scenario Preparing Server for WSUS Installation
Preparing Server for WSUS Installation Downloading & Installing WSUS
Downloading & Installing WSUS
 Configuring WSUS in New York Office
Configuring WSUS in New York Office Downloading, Installing & Configuring WSUS in Chicago Office
Downloading, Installing & Configuring WSUS in Chicago Office WSUS Install Problem in Dallas Office
WSUS Install Problem in Dallas Office Configuring Computer Groups - Client-Site Targeting
Configuring Computer Groups - Client-Site Targeting Configuring Clients Using Group Policy
Configuring Clients Using Group Policy Approving Updates
Approving Updates Configuring WSUS in Tokyo Office in Replica Mode
Configuring WSUS in Tokyo Office in Replica Mode

Using Active Directory Certificate Services
 What is a Certificate?
What is a Certificate? What is a Certificate Authority (CA)?
What is a Certificate Authority (CA)? What are the Different Types of CAs?
What are the Different Types of CAs? Creating a CA Hierarchy
Creating a CA Hierarchy  How Do I Get a Certificate?
How Do I Get a Certificate? What is Credential Roaming? C2
What is Credential Roaming? C2
 What is a Certificate Revocation List (CRL)?
What is a Certificate Revocation List (CRL)? What is an Online Responder?
What is an Online Responder? Installing Active Directory Certificate Services Role
Installing Active Directory Certificate Services Role Certification Authority Overview
Certification Authority Overview Managing Certification Authority Services
Managing Certification Authority Services Process of Setting Up Online Responder
Process of Setting Up Online Responder
Class 14
Backup and Recovery
 Configuring Shadow Copy Service
Configuring Shadow Copy Service Picking a Storage Location
Picking a Storage Location Setting Up the Schedule
Setting Up the Schedule Manual Shadow Copy
Manual Shadow Copy Using Shadow Copy - Restoring Previous Versions
Using Shadow Copy - Restoring Previous Versions Installing Windows Server Backup Feature
Installing Windows Server Backup Feature Backup Once Wizard - Creating Backup of a Volume
Backup Once Wizard - Creating Backup of a Volume Setting Up Backup Scheduleli>
Setting Up Backup Scheduleli>
 Recovering Individual Files
Recovering Individual Files Recovering a Complete Volume
Recovering a Complete Volume Recovering Operating System
Recovering Operating System Additional Backup Tips
Additional Backup Tips
Class 15
Deploying Terminal Services
 What is Terminal Services?
What is Terminal Services? Additional Role Services
Additional Role Services Globomantics Scenario
Globomantics Scenario Installing TS Role with TS Gateway, TS Web Access, and TS Session
Installing TS Role with TS Gateway, TS Web Access, and TS Session Broker on First Server
Broker on First Server Finishing Up Role Installation
Finishing Up Role Installation Extra Step For TS Role Installation on a Domain Controller
Extra Step For TS Role Installation on a Domain Controller Configuring Session Rules for Terminal Servers on User-By-User Basis
Configuring Session Rules for Terminal Servers on User-By-User Basis  Configuring Session Rules for Terminal Servers with Session Time
Configuring Session Rules for Terminal Servers with Session Time Limits in Group Policy
Limits in Group Policy Configuring Session Rules for Terminal Servers in Terminal Services
Configuring Session Rules for Terminal Servers in Terminal Services Configuration Window
Configuration Window
 Configuring Maximum Connections to Terminal Server
Configuring Maximum Connections to Terminal Server Configuring TS Session Broker
Configuring TS Session Broker Installing TS Role on a Second Server
Installing TS Role on a Second Server Installing Office on First Terminal Server
Installing Office on First Terminal Server Adding the Second Terminal Server to the Farm
Adding the Second Terminal Server to the Farm Installing Office on Second Terminal Server
Installing Office on Second Terminal Server Connecting to SALES_TS_FARM from Client Computer
Connecting to SALES_TS_FARM from Client Computer Upgrading Remote Desktop Connection Utility on Windows XP Client
Upgrading Remote Desktop Connection Utility on Windows XP Client Connecting to Terminal Server Using Web Access
Connecting to Terminal Server Using Web Access Deploying Application Using RemoteAppli>
Deploying Application Using RemoteAppli>
 Testing RemoteApp from a Client Computer
Testing RemoteApp from a Client Computer
Planning for High Availability
 What Does High Availability Mean?
What Does High Availability Mean? DNS Round Robin
DNS Round Robin Network Load Balancing (NLB)
Network Load Balancing (NLB) Failover Clustering
Failover Clustering
 Using RAID
Using RAID Working with SANs
Working with SANs Quorum Models
Quorum Models

Class 17
Certificatio
 New Alphabet Soup for Everyone!
New Alphabet Soup for Everyone! What You Need to Take for Each Credential
What You Need to Take for Each Credential Upgrade Paths for MCSAs/MCSEs
Upgrade Paths for MCSAs/MCSEs How to Sign Up for a Microsoft Exam
How to Sign Up for a Microsoft Exam 70-646 Exam Prep Tips
70-646 Exam Prep Tips Additional Exam Prep Tips
Additional Exam Prep Tips
Bonus Class
Hyper-V Installation
 Our Scenario
Our Scenario New Hyper-V Machine Configuration
New Hyper-V Machine Configuration Creating a New Single Volume
Creating a New Single Volume Installing Hyper-V Role
Installing Hyper-V Role Creating a New Hyper-V Machineli>
Creating a New Hyper-V Machineli>
 Virtual Machine Connection Window Buttons
Virtual Machine Connection Window Buttons Installing Virtual Windows 2008
Installing Virtual Windows 2008 Installing Virtualization Extensions
Installing Virtualization Extensions
MCITP PAPER 04
Windows 7 Training Course Outline
 About Your Instructor
About Your Instructor
 About the Course
About the Course
 How to Use the Course
How to Use the Course

Class 2 - Lab Setup
 Scenario Network Configuration
Scenario Network Configuration
 Lab Overview
Lab Overview
Class 3 - The Course Scenario
 Globomantics’ Regulatory Compliance, Security and Budgetary Concerns
Globomantics’ Regulatory Compliance, Security and Budgetary Concerns
 Globmantics’ Office Structure, Technology Challenges and Needs
Globmantics’ Office Structure, Technology Challenges and Needs
 Windows 7 Project Plan
Windows 7 Project Plan
 User Interface Enhancements
User Interface Enhancements
 BranchCache
BranchCache
 DirectAccess
DirectAccess
 BitLocker and BitLocker To Go
BitLocker and BitLocker To Go
 AppLocker
AppLocker
 Windows XP Mode
Windows XP Mode
 Improved Power Management
Improved Power Management
 32-bit vs. 64-bit
32-bit vs. 64-bit
 Editions Comparison Matrix
Editions Comparison Matrix

Class 5 - Installing Windows 7
 Identifying Windows 7 Requirements
Identifying Windows 7 Requirements
 Running the Windows 7 Upgrade Advisor Tool
Running the Windows 7 Upgrade Advisor Tool
 Upgrade and Migration Limitations
Upgrade and Migration Limitations
 Windows 7 Installation Options and Types
Windows 7 Installation Options and Types
 Performing a Clean Installation of Windows 7
Performing a Clean Installation of Windows 7
 Upgrading Windows Vista to Windows 7
Upgrading Windows Vista to Windows 7
 Dual Booting Windows 7
Dual Booting Windows 7
 Windows XP to Windows 7 Dual Boot Walkthrough
Windows XP to Windows 7 Dual Boot Walkthrough
 Migrating User Profiles and Data to Windows 7
Migrating User Profiles and Data to Windows 7
Class 6 - Deploying Windows 7 Machines
 Windows 7 Deployment Enhancements
Windows 7 Deployment Enhancements
 Deployment Types, Thick vs. Thin Images and Deployment Tools and Options
Deployment Types, Thick vs. Thin Images and Deployment Tools and Options
 Capture and Deployment Process Overview and Prerequisites
Capture and Deployment Process Overview and Prerequisites
 Building and Validating the Answer File
Building and Validating the Answer File
 Building and Generalizing the Reference Installation
Building and Generalizing the Reference Installation
 Creating Bootable Windows PE Media
Creating Bootable Windows PE Media
 Capturing the Reference Image and Saving to a Network Share
Capturing the Reference Image and Saving to a Network Share
 Deploying to a Target Computer via Network Share
Deploying to a Target Computer via Network Share
 User State Migration Tool and Automated Installation
User State Migration Tool and Automated Installation
 Using Device Manager
Using Device Manager
 Using the System Information Utility
Using the System Information Utility
 Understanding Drivers and Installation Methods
Understanding Drivers and Installation Methods
 Managing Device and Driver Security
Managing Device and Driver Security
 Updating and Rolling Back Drivers
Updating and Rolling Back Drivers
 The Driver Verifier Utility
The Driver Verifier Utility
 Managing Hardware Installation Policies with Group Policy
Managing Hardware Installation Policies with Group Policy
 Adding Device Drivers to the Driver Store
Adding Device Drivers to the Driver Store
 Monitoring USB Devices
Monitoring USB Devices
Class 8 - Understanding Windows 7 Storage Options
 Deconstructing Basic Disks
Deconstructing Basic Disks
 Master Boot Record vs. GUID Partition Table Disks
Master Boot Record vs. GUID Partition Table Disks
 Understanding Dynamic Disks
Understanding Dynamic Disks
 Dynamic Disk Volume Types
Dynamic Disk Volume Types
 Managing Storage Volumes
Managing Storage Volumes
 Creating Storage Volumes with the Disk Management Tool
Creating Storage Volumes with the Disk Management Tool
 Checking Disks for Errors and Defragmenting Disks
Checking Disks for Errors and Defragmenting Disks
Class 9 - Configuring Networking in Windows 7
 Managing Network Connections
Managing Network Connections
 Managing Wireless Networks in Windows 7
Managing Wireless Networks in Windows 7
 TCP/IP Recap
TCP/IP Recap
 Configuring TCP/IP Settings
Configuring TCP/IP Settings
 IP Addressing
IP Addressing
 IPv6 Recap
IPv6 Recap
 Managing TCP/IP Settings fromn the Command Line
Managing TCP/IP Settings fromn the Command Line
 Configuring Network Adapters
Configuring Network Adapters
 Configuring Internet Connection Sharing
Configuring Internet Connection Sharing
 Troubleshooting Network Connectivity
Troubleshooting Network Connectivity
 Network Profiles / Network Location Awareness
Network Profiles / Network Location Awareness
 Windows Firewall Purpose and Capabilities
Windows Firewall Purpose and Capabilities
 Allowing New Programs Access
Allowing New Programs Access
 Configuring Firewall Notification Settings and Resetting Firewall Defaults
Configuring Firewall Notification Settings and Resetting Firewall Defaults
 Remote Desktop
Remote Desktop
 Remote Assistance
Remote Assistance
 Windows Remote Management Service (WinRM)
Windows Remote Management Service (WinRM)
 WinRM and PowerShell
WinRM and PowerShell
Class 11 - Protecting Windows 7: Local
 Deconstructing Basic Disks
Deconstructing Basic Disks
 Master Boot Record vs. GUID Partition Table Disks
Master Boot Record vs. GUID Partition Table Disks
 Understanding Dynamic Disks
Understanding Dynamic Disks
 Dynamic Disk Volume Types
Dynamic Disk Volume Types
 Managing Storage Volumes
Managing Storage Volumes
 Creating Storage Volumes with the Disk Management Tool
Creating Storage Volumes with the Disk Management Tool
 Checking Disks for Errors and Defragmenting Disks
Checking Disks for Errors and Defragmenting Disks
Class 12 - Managing Mobility Options
 Using Offline Files
Using Offline Files
 Managing File Versions with Sync Center
Managing File Versions with Sync Center
 Transparent Caching
Transparent Caching
 Configuring Local Power Settings and Policies
Configuring Local Power Settings and Policies
 Creating, Exporting and Importing Power Plans
Creating, Exporting and Importing Power Plans
 Location Aware Printing
Location Aware Printing
 An Overview of Updates
An Overview of Updates
 Configuring Important Update Settings
Configuring Important Update Settings
 Reviewing Update History
Reviewing Update History
 Deciding Which Updates to Install
Deciding Which Updates to Install
 Uninstalling Updates
Uninstalling Updates
 Using the Microsoft Baseline Security Analyzer
Using the Microsoft Baseline Security Analyzer
 Using Group Policy to Configure Updates
Using Group Policy to Configure Updates
 WSUS and Windows Updates
WSUS and Windows Updates

Class 14 - Managing Applications
 Program Compatibility Assistant
Program Compatibility Assistant
 Program Compatibility Properties
Program Compatibility Properties
 Application Compatibility Toolkit
Application Compatibility Toolkit
 Using Windows XP Mode
Using Windows XP Mode
 Installing Windows XP Mode and Running Virtual Applications
Installing Windows XP Mode and Running Virtual Applications
 Configuring Software Restriction Policies
Configuring Software Restriction Policies
 Creating Rules with Software Restriction Policies
Creating Rules with Software Restriction Policies
 Using AppLocker
Using AppLocker
 Implementing AppLocker Rules
Implementing AppLocker Rules
Class 15 - Managing Internet Explorer
 Compatibility Mode
Compatibility Mode
 Configuring IE Security Settings
Configuring IE Security Settings
 Managing IE Add-ons and Search Providers
Managing IE Add-ons and Search Providers
 Managing IE’s InPrivate Browsing and InPrivate Filtering
Managing IE’s InPrivate Browsing and InPrivate Filtering
 About IE’s SmartScreen Filter
About IE’s SmartScreen Filter
 IE’s Pop-Up Blocker
IE’s Pop-Up Blocker
 Managing IE Certificates
Managing IE Certificates

 Changing File and Folder Permissions
Changing File and Folder Permissions
 Understanding NTFS Permissions
Understanding NTFS Permissions
 Assigning NTFS Permissions
Assigning NTFS Permissions
 Understanding Effective Permissions
Understanding Effective Permissions
 Permissions Impact: Copying and Moving Files
Permissions Impact: Copying and Moving Files
 Encrypting Files and Folders Using EFS
Encrypting Files and Folders Using EFS
 BitLocker To Go
BitLocker To Go
 Full Disk Encryption Using BitLocker
Full Disk Encryption Using BitLocker
 Configuring and Managing BitLocker Drive Encryption
Configuring and Managing BitLocker Drive Encryption
 Using the BitLocker PIN Option
Using the BitLocker PIN Option
Class 17 - Shared Access to Resources
 Resource Sharing Overview
Resource Sharing Overview
 Basic vs. Advanced Sharing
Basic vs. Advanced Sharing
 Understanding Share vs. NTFS Permissions
Understanding Share vs. NTFS Permissions
 Offline Folder Caching
Offline Folder Caching
 Sharing Folders
Sharing Folders
 Sharing Printers and Managing Print Queues
Sharing Printers and Managing Print Queues
 Windows 7 Libraries
Windows 7 Libraries
 Configuring HomeGroup
Configuring HomeGroup
Class 18 - Using DirectAccess and VPN Connections
 DirectAccess Features, Requirements and Connection Methods
DirectAccess Features, Requirements and Connection Methods
 Configuring DirectAccess with Group Policy
Configuring DirectAccess with Group Policy
 Configuring DirectAccess from the Command Line
Configuring DirectAccess from the Command Line
 Enabling VPN-Based Remote Access
Enabling VPN-Based Remote Access
 VPN Authentication Mechanisms
VPN Authentication Mechanisms
 Windows 7 VPN Connections
Windows 7 VPN Connections
 Understanding BranchCache
Understanding BranchCache
 BranchCache Operating Modes
BranchCache Operating Modes
 Managing BranchCache with Group Policy
Managing BranchCache with Group Policy
 Managing BranchCache with Netsh
Managing BranchCache with Netsh
 Monitoring BranchCache
Monitoring BranchCache

Class 20 - Monitoring and Maintaining Windows 7
 Performing Information and Tools
Performing Information and Tools
 Configuring Event Logging
Configuring Event Logging
 Saving and Exporting Log Files
Saving and Exporting Log Files
 Centralizing Event Logs
Centralizing Event Logs
 Using Performance Monitor
Using Performance Monitor
 Data Collector Sets
Data Collector Sets
 Customizing Built-In Data Collector Sets to Troubleshoot Specific Issues
Customizing Built-In Data Collector Sets to Troubleshoot Specific Issues
 Creating a New Data Collector Set
Creating a New Data Collector Set
 Task Manager
Task Manager
 Resource Monitor
Resource Monitor
 Reliability Monitor
Reliability Monitor
 A Sample WMI Script
A Sample WMI Script
Class 21 - Configuring Performance Settings
 Changing Graphics Settings
Changing Graphics Settings
 Configuring Virtual Memory
Configuring Virtual Memory
 Understanding Write Caching
Understanding Write Caching
 Optimizing Processes with Task Manager
Optimizing Processes with Task Manager
 Managing Processor Scheduling Settings
Managing Processor Scheduling Settings
 Optimizing Services
Optimizing Services
 Using Msconfig to Boost Performance
Using Msconfig to Boost Performance

 Windows 7’s Backup and Restore Utility
Windows 7’s Backup and Restore Utility
 Configuring Windows Backup
Configuring Windows Backup
 Restoring Files from a Backup
Restoring Files from a Backup
 Creating and Restoring System Images
Creating and Restoring System Images
 Creating a System Repair Disk
Creating a System Repair Disk
 Creating and Using System Restore Points
Creating and Using System Restore Points
 Understanding Advanced Boot Options
Understanding Advanced Boot Options
 Understanding Last Known Good Configuration
Understanding Last Known Good Configuration
Class 23 - Preparing for TS: Windows 7, Configuring (70-680)
 The Candidate Profile
The Candidate Profile
 Skills Being Measured
Skills Being Measured
 Objective to Lesson Mapping
Objective to Lesson Mapping
 Study Recommendations and Exam Prep Tips
Study Recommendations and Exam Prep Tips
 Credit Toward Certification
Credit Toward Certification
Class 24 - Next Steps
 Where You Started
Where You Started
 What You’ve Accomplished
What You’ve Accomplished
 My Favorite Suporting Resources
My Favorite Suporting Resources
 We Value Your Opinion
We Value Your Opinion
MCITP PAPER 05
Windows Server 2008 Enterprise Administrator Training - Course Outline
Welcome to Windows Server 2008 Enterprise Administrator
Of course, we have to start out with the standard "here's-what-you-can-expect-in-the-course." In this Class you'll get to learn a little bit about your instructor, what you can expect from this course, and the hardware I used to create the demonstrations in the course. About Your Instructor
About Your Instructor
 What's Covered in this Course
What's Covered in this Course
 Hardware
Hardware

Class 2
To Virtualize or Not To Virtualize: When Hyper–V is a Good Idea, and When It's Not
You know that Virtualization is hot right now and it shows no signs of cooling off. In this Class we’ll talk about when Hyper–V is a good idea, when it’s a bad idea, and when to implement Hyper–V in your network A Quick Refresher on Virtualization
A Quick Refresher on Virtualization
 Licensing and Versions
Licensing and Versions
 Candidates for Virtualization
Candidates for Virtualization
 Your Virtualization Migration Tools
Your Virtualization Migration Tools
 Running sysprep and Capturing Image
Running sysprep and Capturing Image
 Creating New Hyper-V Machine
Creating New Hyper-V Machine
 Windows Setup Wizard
Windows Setup Wizard
 Globomantics Virtualization Plan
Globomantics Virtualization Plan
Class 3
Active Directory Forest Design and Functional Levels
Designing your Active Directory Forest and Functional Levels is a multi–faceted process. In this Class you will learn about the components and considerations help you make those critical decisions when setting up or redesigning an Active Directory environment. How To "Plant" A Forest
How To "Plant" A Forest
 Domains and Trees In The Forest
Domains and Trees In The Forest
 To Upgrade or Not To Upgrade?
To Upgrade or Not To Upgrade?
 Sites: Yet Another Thing to Deal With
Sites: Yet Another Thing to Deal With
 Globomantics AD Structure Stateside
Globomantics AD Structure Stateside
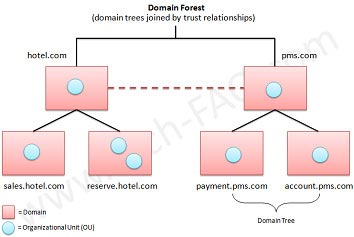
 What Are Trusts
What Are Trusts
 The Types of Trusts
The Types of Trusts
 Rules of Engagement
Rules of Engagement
 Verdepetra.com Buyout Plan
Verdepetra.com Buyout Plan
 Creating Forest Trust
Creating Forest Trust
Class 5
Active Directory Group and Group Policy Strategy
Learn multiple ways to design your Organizational Unit and Group Structure. Plus, we will work with AGUDLP and learn how to create Starter Policies for Group Policy and Fine Grained Password Policies. Organizational Units and Groups
Organizational Units and Groups
 AGUDLP
AGUDLP
 Configuring AGUDLP
Configuring AGUDLP
 Shadow Group
Shadow Group
 Group Policy
Group Policy
 Starter Policies
Starter Policies
 Group Policy Preferences
Group Policy Preferences
 Fine Grained Password Policies
Fine Grained Password Policies
 Creating Fine Grained Password Policy
Creating Fine Grained Password Policy
Class 6
Active Directory Backup and Recovery
Learn to use NTDSUTIL to perform high-level maintenance on your Active Directory database. Plus, you will see how to optimize an IFM Backup and identify Operations Masters (FSMO’s) and where they should go. NTDSUTIL
NTDSUTIL
 Creating Install from Media (IFM) Backup
Creating Install from Media (IFM) Backup
 Tombstone Lifetime
Tombstone Lifetime
 How to Seize Operations Master from a Dead Domain Controller
How to Seize Operations Master from a Dead Domain Controller
 Seizing a Role
Seizing a Role
DNS: Your Name Resolution Solution
Getting your clients to be able to find what they need on your network is a critical part of your network design. In this Class you'll see the benefits of Active Directory Integrated DNS, set up a GlobalNames zone, and learn fun facts about Forwarders and Stub Zones. New Features in DNS
New Features in DNS
 To Integrate into AD or Not to Integrate
To Integrate into AD or Not to Integrate
 Conditional Forwarders vs. Stub Zones
Conditional Forwarders vs. Stub Zones
 Who WINS Nowadays?
Who WINS Nowadays?
 Creating GlobalNames Zones
Creating GlobalNames Zones
 IPv6 Basic Configuration
IPv6 Basic Configuration
Class 8
Active Directory Certificate Services
Security continues to be a top priority for any company or individual, and running your own Public Key Infrastructure can be at the center of your internal security solution. In this Class, not only will you learn how to set up an Enterprise Root Authority, but you will also learn how to set it up so that users can get their own certificates. Introduction to Public Key Infrastructure
Introduction to Public Key Infrastructure
 The Root Authority
The Root Authority
 Subordinate Servers
Subordinate Servers
 Revocation Lists – the CRL
Revocation Lists – the CRL
 The Online Responder
The Online Responder
 Versions and CA Role Services
Versions and CA Role Services
 Globomantics Scenario
Globomantics Scenario
 Installing Enterprise Root Authority
Installing Enterprise Root Authority
 Managing PKI
Managing PKI
 Creating Domain Certificate
Creating Domain Certificate
 Requesting Certificates
Requesting Certificates
Class 9
How To Get Out Of The Office With Terminal Services
Out of all the enhancements in Server 2008, Terminal Services may just be one of my favorites. Planning out a Terminal Services implementation requires knowledge of what is available and where stuff needs to go. Remote App vs. Remote Destop
Remote App vs. Remote Destop
 On the Go with Web Access
On the Go with Web Access
 Implementing TS Server
Implementing TS Server
 TS Remote Apps Manager Overview
TS Remote Apps Manager Overview
 Getting Out of the Office with TS Gateway
Getting Out of the Office with TS Gateway
 Keeping Your Users Happy with High Availability
Keeping Your Users Happy with High Availability
 Creating a Capture Boot Image
Creating a Capture Boot Image
 Running sysprep on TS1
Running sysprep on TS1
 Capturing the Image on TS1
Capturing the Image on TS1
 Creating a Brand New Server
Creating a Brand New Server
 Deploying Images Using Deployment Services
Deploying Images Using Deployment Services
 Installing TS Session Broker
Installing TS Session Broker

Rights Management and Distributed File System
Securing your data as well as allowing people to, oh I don't know, ACTUALLY USE IT, can be a tricky endeavor. Using RMS and DFS together can not only secure your data, but allow access only to the users who need it. Share Your Stuff Safely with Rights Management
Share Your Stuff Safely with Rights Management
 Get Your Stuff Out There with DFS
Get Your Stuff Out There with DFS
 Installing DFS Role Service
Installing DFS Role Service
 Utilizing DFS – Creating Replication Group
Utilizing DFS – Creating Replication Group
 GloboFilesGroup Actions Overview
GloboFilesGroup Actions Overview
 Testing Replication
Testing Replication
 Publishing Points
Publishing Points
 Creating a Namespace
Creating a Namespace
 Combining DFS and RMS
Combining DFS and RMS
Class 11
Keep Your Apps Online with High Availability
Let's face it—your users (or “internal customers” if you're cool) want access to applications they need to do their work, and they want it now. High availability tools like Failover Clustering and Network Load Balancing can help you to provide a higher level of experience to users even when some of your machines “blow up.” Failover Clustering
Failover Clustering
 Quorum Disk
Quorum Disk
 Network Load Balancing
Network Load Balancing
 Globomantics Scenario
Globomantics Scenario
 Installing Network Load Balancing Feature
Installing Network Load Balancing Feature
 Creating a New Cluster
Creating a New Cluster
 Adding DNS Entry for Our Cluster
Adding DNS Entry for Our Cluster
 Adding Machines to a Cluster
Adding Machines to a Cluster
 Verifying that Network Load Balancing is Working
Verifying that Network Load Balancing is Working
 Creating Single Name Resolution with GlobalNames
Creating Single Name Resolution with GlobalNames
Class 12
The Read–Only Domain Controller
Branch offices are a big reality, but when users in those offices go to do something simple like logon to the network, it can take more time than normal if you don't have a Read-Only Domain Controller. In this Class, you'll learn why RODC’s can be very beneficial in these remote offices. Where Would an RODC Go?
Where Would an RODC Go?
 How To Install a Full RODC
How To Install a Full RODC
 Drawbacks to RODCs
Drawbacks to RODCs
 Installing RODC
Installing RODC
 Verifying Installation
Verifying Installation
 Taking a Look at Answer File
Taking a Look at Answer File
 Full RODC or Server Core?
Full RODC or Server Core?
 Branch Office Stuff You Need to Know
Branch Office Stuff You Need to Know
WSUS: Keeping Your Machines Updated
Using Automatic Updates directly from Microsoft’s server is nifty but depending on the amount of machines you have in your enterprise; just keeping security updates installed on your clients and servers can use up a massive amount of bandwidth. In this Class, you'll learn how to set up WSUS and control the updates that get pushed down to your machines. Three Update Methods
Three Update Methods
 Windows Server Update Services – WSUS
Windows Server Update Services – WSUS
 Managing WSUS
Managing WSUS
 Downloading and Installing WSUS
Downloading and Installing WSUS
 Configuring WSUS Server
Configuring WSUS Server
 Adding Computers to WSUS Server
Adding Computers to WSUS Server
 Configuring Group Policy
Configuring Group Policy
 Approving Security Updates on WSUS
Approving Security Updates on WSUS
 Running Updates on Vista Client
Running Updates on Vista Client
 WSUS Administrator Group
WSUS Administrator Group
 System Center
System Center

Class 14
Active Directory Certificate ServicesLock It Up: Security Made Semi–Easy
Microsoft provides some great tools to help lock down your server. In this Class I&rsauo;ll show you three great solutions to reduce your attack surface on your servers. BitLocker
BitLocker
 Security Configuration Wizard Overview
Security Configuration Wizard Overview
 Running Security Configuration Wizard
Running Security Configuration Wizard
 Locating the Policy on Hard Drive
Locating the Policy on Hard Drive
 Baseline Security Analyzer
Baseline Security Analyzer
Class 15
Planning for Remote Access
This Exam Prep Class provides you with the core considerations that you’ll need to examine when planning your design for Remote Access. There are actually three networks that you need to plan for, and we will talk about all of them so you’ll know what areas you need to work with. Networks that You Have to Plan for
Networks that You Have to Plan for
 NPS and RADIUS: Not Just for Dial–Up Anymore
NPS and RADIUS: Not Just for Dial–Up Anymore
 Network Access Policy – NAP
Network Access Policy – NAP
 Methods for NAP Enforcement
Methods for NAP Enforcement
